Risk and analysis is the process of identifying, assessing, and neutralizing potential threats to your business—your operations, your assets, and most importantly, your customer data. For a startup or SMB, this isn't just about defence. It's a strategic move to show enterprise clients you're a mature, trustworthy partner. Mastering it helps you fly through the security questionnaires that stall sales deals and builds the foundation for critical compliance frameworks like ISO 27001 and SOC 2.
Why Risk and Analysis Is Your Startup’s Secret Weapon to Close Deals

Let's cut to the chase. That massive enterprise deal you've been chasing? It’s likely stuck in procurement because of a lengthy security questionnaire. This is the exact moment where risk and analysis stops being a theoretical chore and becomes your most powerful sales tool. For startups and SMBs, proving you have a solid handle on security isn't just a nice-to-have; it's the non-negotiable price of entry to win high-value enterprise clients.
This isn’t about creating massive binders of documents that just sit on a shelf. A smart, actionable approach to risk and analysis is about building rock-solid trust. It signals to potential customers that you’re a serious partner who protects their data as if it were your own. It’s how you ace security due diligence, prove your company is mature beyond its years, and gain a massive competitive advantage.
Moving Beyond a Compliance Chore
Too many founders see risk management as a corporate headache—a bureaucratic process that slows down their fast-moving startup. That’s a myth, and it’s a costly one. When you systematically identify, analyse, and treat your risks, you’re not just prepping for an audit. You’re building a more resilient, efficient, and ultimately more valuable business that enterprise customers want to buy from.
This proactive mindset directly solves the pain points that kill momentum and stall growth:
- Faster Sales Cycles: Stop getting bogged down by security reviews. With a documented risk assessment, you can answer those lengthy security questionnaires with speed and confidence, impressing procurement teams and shortening your sales cycle.
- Unlock Enterprise Deals: Large companies will not do business with vendors who can't demonstrate a mature security program. A formal risk analysis is your proof.
- Simplified Compliance: A proper risk analysis is the cornerstone for certifications like ISO 27001, NIS 2, DORA, and SOC 2. It’s the first thing auditors look for and makes the entire process smoother.
Think of a formal risk and analysis process as your security story. It tells clients and auditors a clear, compelling narrative that you not only know where your weaknesses are but have a concrete plan to manage them. That builds confidence and dramatically shortens due diligence.
The Growing Importance of a Formal Process
The demand for structured risk management is only getting more intense. In France, for example, the cybersecurity market is on track to hit USD 14,297.5 million by 2030, fuelled by a massive spike in cyberattacks. A jaw-dropping 49% of French firms were hit by significant incidents in 2022, a huge jump from 34% just the year before. You can dive deeper into these cybersecurity market findings on grandviewresearch.com.
This trend has pushed risk analysis from a technical IT task right into the boardroom. For your startup, it means that winging it with ad-hoc security measures just won't cut it anymore. Mastering a formal risk and analysis process is how you demonstrate credibility, meet complex compliance demands, and finally, close the deals that will fuel your growth.
Qualitative vs. Quantitative Analysis: Choosing the Right Approach
So, you’ve decided to tackle risk analysis head-on. Excellent choice. The first question that pops up is always, "Where do I even start?" The decision often comes down to two main flavours of analysis: qualitative and quantitative. It sounds academic, but the distinction is actually quite practical and will shape how you approach your entire security programme.
Think of it like checking the weather. A qualitative analysis is like glancing out the window, seeing dark clouds, and thinking, "Looks like rain." It’s an assessment based on experience, intuition, and observation—it’s quick, practical, and gets you to an actionable result without needing complex data models.
A quantitative analysis, on the other hand, is the full meteorologist's report. It uses hard data and complex models to tell you, "There is an 80% probability of one inch of rain between 2 p.m. and 4 p.m., with a potential financial impact of €50,000 in event damages." This method is all about attaching real numbers—probabilities and financial costs—to each risk.
The Startup's Dilemma: When to Use Each Approach
For an early-stage startup or SMB, a qualitative analysis is almost always the right place to start. Why? Because your primary pain point is needing to quickly map out the biggest threats to your business without getting lost in complex statistical models. You need actionable insights, fast.
A qualitative approach lets you categorise risks on a simple scale—like Low, Medium, or High—for both their likelihood and potential impact. This helps you build your first risk heatmap and immediately see where you need to focus your limited time and resources. It answers the crucial question: "What are the biggest fires we need to put out right now?"
The real magic of qualitative analysis for a startup is its speed and accessibility. You can get your leadership team in a room for a few hours and walk out with a solid risk register that gives your security efforts immediate direction.
Quantitative analysis tends to come into play as your company matures or when you need to meet specific regulatory demands. For instance, financial frameworks like DORA expect more data-driven, quantifiable proof of your risk management. It's also an incredibly powerful tool for getting budget approval. Pitching a €20,000 security control is much easier when you can show it mitigates a potential €250,000 loss from a data breach. That kind of language gets attention.
Qualitative vs. Quantitative Risk Analysis At A Glance
To help you decide what’s right for your business right now, here’s a quick comparison. Think of it as a cheat sheet for choosing your path based on your current stage and compliance needs.
| Attribute | Qualitative Analysis | Quantitative Analysis |
|---|---|---|
| Best For | Early-stage startups, initial risk assessments, and quick prioritisation. | Mature companies, high-stakes decisions, and justifying security budgets. |
| Output | Risks categorised as High, Medium, or Low on a risk matrix or heatmap. | Risks assigned specific financial values (€) and probability percentages (%). |
| Effort | Low to moderate. Based on expert opinion, workshops, and experience. | High. Requires historical data, statistical models, and specialised tools. |
| Compliance | Fully acceptable for ISO 27001, which offers flexibility in methodology. | Often preferred for stricter frameworks like DORA or for financial audits. |
At the end of the day, a standard like ISO 27001 doesn’t force you into one camp. The most important thing is to choose a method, stick with it consistently, and clearly document your reasoning. For most startups, a qualitative analysis delivers the most bang for your buck early on and builds a fantastic foundation for a more numbers-driven approach down the road.
A Step-By-Step Guide to ISO 27005 Risk Analysis
Let’s be honest: tackling a formal risk analysis process can feel like a huge, academic chore. But it doesn't have to be. By following the roadmap laid out in ISO 27005—the gold standard for information security risk management—you can build a process that's not just structured and repeatable, but also easy for auditors to understand. Think of it as the essential blueprint for a successful ISO 27001 certification.
We've distilled the official guidance into a practical, five-step playbook designed for anyone from a startup founder to a technical lead. The goal is to transform risk analysis from an abstract concept into a concrete action plan that strengthens your security programme.
This flowchart maps out how both qualitative (judgment-based) and quantitative (data-driven) approaches feed into a well-structured risk analysis process.
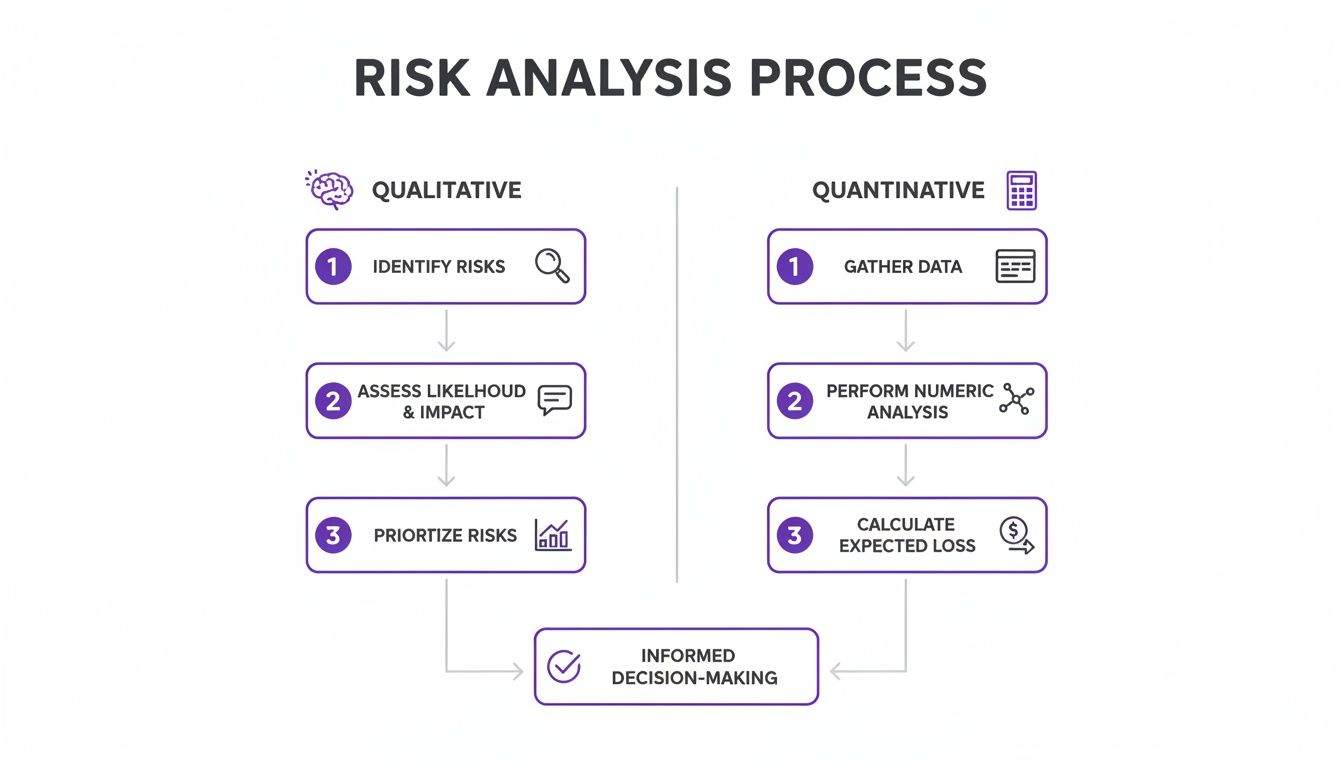
As you can see, the path from spotting a threat to making a smart decision is logical, no matter which specific technique you end up using.
Step 1: Identify the Risks
First things first: you can't protect what you don't know you have. This initial step is all about mapping out your information assets—the critical data and systems your business simply cannot function without.
For a typical SaaS startup, that list will probably include:
- Customer Data: All the PII, usage stats, and payment details sitting in your main database.
- Source Code: Your company's secret sauce, hosted in a Git repository like GitHub or GitLab.
- Cloud Infrastructure: The servers, databases, and network gear running on AWS, Azure, or Google Cloud.
- Third-Party Services: The essential SaaS tools you lean on daily, like your CRM, payment gateway, or marketing platform.
With your asset inventory complete, you can start pinpointing the threats (what could go wrong) and the vulnerabilities (the weaknesses that let the threats in). A risk materialises right at the intersection of an asset, a threat, and a vulnerability.
SaaS Example:
- Asset: Customer database on AWS.
- Threat: A disgruntled ex-employee who still has their access credentials.
- Vulnerability: A manual and inconsistent employee offboarding process.
- Risk: An unauthorised ex-employee gains access to sensitive customer data.
Step 2: Analyse the Risks
Now that you have a list of potential risks, it’s time to analyse them. Here, you'll figure out their potential impact and how likely they are to happen, which is key for prioritisation. Using the qualitative method favoured by most startups, you'll assign a simple rating (like Low, Medium, or High) to both of these dimensions.
- Likelihood: How probable is it that this scenario will actually play out? Consider past incidents, the current threat landscape, and any controls you already have in place.
- Impact: If it does happen, how bad will it be? Think about financial losses, damage to your reputation, legal trouble, and operational chaos.
For our disgruntled ex-employee example, the analysis might look something like this:
- Likelihood: Medium. If your offboarding is haphazard, it’s quite possible someone’s access gets overlooked.
- Impact: High. Unauthorised access to your entire customer database could trigger a massive data breach, destroy your reputation, and bring down heavy fines under GDPR.
Step 3: Evaluate the Risks
It's time to pull it all together. By plotting each risk on a matrix—with likelihood on one axis and impact on the other—you create a risk heatmap. This visual tool makes your priorities instantly clear.
Any risks landing in the high-impact, high-likelihood quadrant (usually coloured red) need your immediate attention. Those in the low-impact, low-likelihood corner (green) can probably be accepted or dealt with later. This evaluation is where you define your company's risk appetite: the amount of risk you're willing to live with to achieve your goals.
For a deeper look at building out a solid framework, check out our guide on https://compli.st/blog/risk-management-iso-27005.
Step 4: Treat the Risks
With your risks evaluated and prioritised, you need a game plan. ISO 27005 gives you four main ways to treat a risk. The right choice depends on the risk's severity, the cost of fixing it, and your overall business strategy.
- Mitigate: This is the most common response. You implement security controls to lower the risk's likelihood or its potential impact.
- Transfer: You shift the financial fallout of a risk to someone else, most often by buying a cybersecurity insurance policy.
- Avoid: You simply stop doing the activity that creates the risk. For instance, you might decide not to collect a certain type of sensitive data in the first place.
- Accept: You make a conscious, documented decision to live with the risk, usually because the cost of treatment is far greater than the potential damage.
For our ex-employee risk, the only sensible choice is to mitigate. The fix? Implement a bulletproof, checklist-driven offboarding process that ensures every single access credential—from cloud consoles to SaaS logins—is revoked on an employee's last day.
Step 5: Monitor and Review
Finally, remember that risk analysis isn't a one-and-done project. It's a continuous cycle. Threats change, your business grows, and new vulnerabilities pop up all the time. You have to regularly monitor your risks and make sure your controls are still effective. To stay aligned with standards like ISO 27005, it helps to use modern compliance-friendly AI BI solutions that prioritize legal security.
Make a habit of reviewing your risk register at least once a year, or whenever something significant changes, like launching a new product. This ongoing vigilance keeps your security posture relevant and ensures you're ready for both audits and real-world attacks.
Turning Your Risk Analysis Into Actionable Deliverables

A risk analysis is completely useless if it just sits in a spreadsheet, gathering dust. To make it a powerful tool that impresses auditors and helps you close deals faster, you have to turn your findings into clear, actionable documents. These deliverables are the evidence that proves you have a mature and well-managed security programme.
For a startup or SMB, this is your secret weapon. It’s how you ace security questionnaires and build immediate trust with enterprise customers who demand a high level of security. We’re not talking about abstract theories here; these are the practical tools that turn your risk and analysis work into a real business advantage. Let's focus on the three essential deliverables every growing company needs.
Your Complete Inventory: The Risk Register
Think of the Risk Register as the foundation of your entire risk management effort. It’s your complete, centralised inventory of every potential risk the business faces, from a technical vulnerability in your code to an operational weakness in your onboarding process. It’s the single source of truth that captures what the risk is, why it matters, and what you’re doing about it.
A well-organised register isn’t just a static list; it’s a living, breathing management tool. At a bare minimum, each entry needs to detail the risk itself, its likelihood and impact scores, an assigned owner, and the chosen treatment plan. This is exactly the kind of detail that auditors for frameworks like ISO 27001 are looking for.
For instance, an entry might look something like this:
- Risk ID: R-001
- Description: Lack of a formalised data backup and recovery testing process.
- Impact: High (potential for permanent data loss and extended downtime).
- Likelihood: Medium (backups exist but have never been verified).
- Treatment Plan: Mitigate by implementing and documenting quarterly recovery tests.
Having this ready is invaluable. When a security questionnaire asks, "How do you manage data recovery risks?" you can pull up this entry and give a confident, evidence-backed answer in seconds.
Your Visual Snapshot: The Risk Heatmap
While the risk register holds all the granular details, the Risk Heatmap tells the story at a glance. It's a simple but incredibly effective visual tool that plots each risk on a grid—likelihood on one axis, impact on the other—using a familiar red-amber-green colour scheme. Its entire purpose is to make prioritisation intuitive for everyone, including non-technical executives.
The heatmap immediately draws everyone's eyes to the most critical threats huddled in the top-right corner—the high-impact, high-likelihood risks. This is where your leadership team should be focusing its attention and resources. It answers the crucial question, "What should we fix first?" without anyone needing to wade through a massive spreadsheet.
A risk heatmap is the single most effective way to communicate security priorities to your board. It cuts through the technical jargon and presents a clear, data-driven picture of your risk landscape, making it far easier to justify security investments and get everyone on the same page.
That visual clarity is also a huge asset in sales conversations. When you can show a prospective enterprise client that you have a formal process for visualising and prioritising risks, it demonstrates a level of maturity that builds immense trust.
Your Actionable To-Do List: The Remediation Plan
Finally, the Remediation Plan is where your analysis becomes action. This deliverable is your team's tactical to-do list, laying out the specific steps, timelines, and responsibilities for treating each identified risk. It’s the bridge between knowing there's a problem and actually fixing it.
Every item in the plan should be a concrete task assigned to a specific person or team. Continuing our backup risk example, a remediation task would be something like: "Lead DevOps Engineer to perform a full restore from backups to a staging environment and document the process by the end of Q3."
This document creates accountability and makes your progress measurable. For auditors, a well-defined remediation plan proves your risk analysis isn't just a paper-shuffling exercise; it’s a living process that drives real security improvements. This becomes critical when managing the controls needed for compliance. To see how these controls are structured, you can learn more about the ISO 27001 Annex A controls in our detailed guide. Ultimately, these documents provide the verifiable proof that you are actively managing your security posture—a must-have for closing big deals and passing audits.
Avoiding Common Pitfalls in Your Risk Analysis Journey
Getting a formal risk analysis process off the ground is a huge step in maturing your security programme. But it’s easy to get sidetracked. Too often, what should be a strategic exercise turns into a frustrating, box-ticking chore. Knowing the common traps from the start helps you steer clear and ensure your work actually adds value.
Many smaller businesses and startups trip up by treating risk analysis as a purely theoretical task. They either create generic assessments that have little to do with their actual business or get so bogged down in academic debates that they suffer from 'analysis paralysis'—never getting around to fixing anything. The best approach is always a pragmatic one.
The Dangers of One-Size-Fits-All Analysis
One of the biggest mistakes is grabbing a generic risk template and running with it, without customising it to your specific operations. A risk register for a fintech company handling sensitive payment data should look worlds apart from one for a B2B SaaS platform that only processes basic business info. Relying on a generic list almost guarantees you'll overlook the threats that are most likely to hit you.
Your analysis has to be grounded in your reality. This means getting people from across the business—product, engineering, sales—in a room to pinpoint threats specific to your tech stack, your customers, and how you actually work. At its core, this is about practicing thorough what is due diligence to truly understand your own environment.
Avoiding Analysis Paralysis
Here's another classic pitfall: the quest for the "perfect" risk analysis. I’ve seen teams spend months debating the precise likelihood score of some obscure, far-fetched risk while critical, everyday vulnerabilities go completely unaddressed. This endless loop of discussion without action completely defeats the purpose.
The goal of risk analysis isn't to eliminate all uncertainty. It's to make better, more informed decisions about where to spend your limited time, money, and energy. It's about progress, not perfection.
A simple, practical tip? Just focus on your top 10 or 15 risks to start. Pinpoint the threats that pose the most immediate and significant danger to your business and build your remediation plan around those. This builds momentum and lets you deliver real security improvements, fast.
Risk Management Is a Process, Not a Project
Finally, a lot of organisations treat risk management like a one-off project. They do the analysis, generate the reports to keep an auditor happy, and then shove it all in a drawer until next year. This is a massive mistake because your risks—and the threats that cause them—are changing all the time.
Effective risk and analysis is a living, continuous process. Your risk register should be a dynamic document, one that you revisit and update at least once a year, or whenever something major changes—like launching a new product or expanding into a new market. This constant vigilance keeps your security posture relevant and resilient, turning risk management into a real business advantage, not just a task you have to get through.
How to Automate Your Risk and Analysis with AI

After walking through the manual steps, it’s clear that a proper risk analysis is a major time sink. For startups and lean teams, this is a huge pain point. It can easily consume hundreds of hours that should be spent building your product or talking to customers, all while you're stuck wrestling with spreadsheets and endless meetings. This is exactly where modern compliance automation platforms change the game.
AI-powered tools can handle the entire risk analysis workflow, turning weeks of manual work into a few clicks. But this isn't just about speed; it’s about being smarter and more precise. These systems remove the guesswork from identifying and prioritising risks, giving you a clear, actionable roadmap for your security program that auditors and enterprise clients love.
From Manual Effort to Strategic Advantage
For a growing company, the payoff is immediate. Instead of being bogged down in administrative tasks, your team can get back to building the product and closing deals. AI-driven platforms automatically generate the audit-ready documents and evidence that enterprise clients and auditors expect to see, without the manual effort.
This automated approach directly solves your biggest business challenges:
- Speed Up Sales Cycles: Fly through security questionnaires with accurate, evidence-backed responses generated for you.
- Achieve Compliance Faster: Clear the path to certifications like ISO 27001, SOC 2, DORA, and NIS 2 without the headaches.
- Save Precious Resources: Win back hundreds of engineering and management hours that used to disappear into manual compliance tasks.
By automating risk analysis, you’re not just ticking a compliance box. You’re turning a defensive chore into a proactive sales tool that builds trust and helps you land bigger contracts, even with a lean team.
Meeting Modern Compliance Demands
The demand for better governance, risk, and compliance (GRC) tools is exploding. Take the NIS2 directive in France, which is set to expand compliance duties from about 500 to nearly 15,000 entities. That’s a massive jump. For any business facing third-party audits, getting risk prioritisation wrong is a major red flag.
Platforms that provide prioritised, ISO 27005-aligned remediation plans can slash the time spent on security questionnaires by up to 70%. You can get a better sense of the growing cybersecurity market on mordorintelligence.com.
This is precisely the problem tools like Compli.st’s RiskAI were built to solve. They automate the whole workflow, making solid risk management a reality for any company. To see how these modern platforms compare, check out our guide on the 5 best Vanta alternatives that help businesses automate their security compliance.
Frequently Asked Questions
Getting started with a formal risk analysis programme can feel a bit daunting, especially when you're a startup juggling a dozen other priorities. Here are some straightforward answers to the questions we hear most often.
How Often Should a Startup Conduct a Risk Analysis?
As a rule of thumb, a full-blown risk analysis should be on your calendar at least annually.
But don't just set it and forget it. You'll need to revisit your analysis any time something significant changes in your business. Think major product launches, adopting a new mission-critical piece of software, or entering a new market. Your risk register isn't a static report; it's a living document that should evolve with your company.
Can We Achieve ISO 27001 with a Qualitative Analysis?
Yes, you certainly can. The ISO 27001 standard is flexible and doesn't mandate one specific method over another. For most startups and small to medium-sized businesses, a well-documented qualitative analysis is not only acceptable but is often the most sensible and efficient place to start.
What auditors really care about is consistency. Whichever method you choose, you need to apply it systematically across the board. They want to see a repeatable process that produces comparable results year after year, proving your approach is organised and mature.
What Is the Difference Between a Risk Analysis and a Vulnerability Assessment?
It's a common point of confusion, but the distinction is important.
Imagine a vulnerability assessment as a mechanic inspecting your car for potential weak spots—worn-out brake pads, an old filter, a leaky hose. It's a technical check-up that identifies specific flaws, like an unpatched server or a flimsy password policy.
A risk and analysis process takes a much wider, strategic view. It asks, "What's the likelihood someone actually cuts those brakes, and what would the damage be if they did?" It weighs the probability of a threat exploiting a vulnerability against the real-world business impact. In short, a vulnerability is just one ingredient in the much larger recipe of risk.
Who Should Be Involved in the Risk and Analysis Process?
Risk analysis is a team sport, not a solo mission for the IT department. To get a true picture of your risk landscape, you need perspectives from every corner of the business. Confining it to a technical silo is a classic mistake.
You'll want to pull in a few key people:
- Leadership: Your CEO and CTO need to be at the table to provide strategic context and champion the entire effort.
- Department Heads: Getting insights from the heads of product, engineering, legal, sales, and HR is non-negotiable. They understand the operational realities and potential impacts in a way no one else can.
Ready to turn your risk and analysis from a manual headache into a powerful sales tool? Compli.st's RiskAI conducts an ISO 27005-aligned analysis in minutes, delivering the audit-ready heatmaps and remediation plans you need to build trust and grow your business. Discover how Compli.st can help you close deals faster.