At its core, the difference is simple: ISO 27001 is the standard you get certified against. It defines what your organisation must do to establish, implement, and maintain a formal Information Security Management System (ISMS). It's the blueprint for compliance.
In contrast, ISO 27002 is the detailed implementation guide. It explains how to apply the security controls needed to meet ISO 27001's requirements. Think of it as the construction manual. You can’t get certified against ISO 27002, but achieving ISO 27001 certification without its guidance is nearly impossible.
Understanding The Core Difference: What vs. How

For startups and SMBs, navigating cybersecurity frameworks like ISO can feel overwhelming. The first pain point is often just understanding how ISO 27001 and ISO 27002 fit together. Getting this wrong can waste months of effort and budget.
Let's use a clear analogy. Imagine you need to build a secure data center.
ISO 27001 is the architectural plan. It mandates that the facility must have reinforced walls, secure access points, and a surveillance system. It sets the non-negotiable requirements for what a secure building is, but it won't specify the brand of lock or the type of camera you must install.
ISO 27002 is the detailed construction manual. This guide offers best practices for everything: installing those locks correctly, positioning cameras for optimal coverage, and choosing the right materials for the walls. It gives your technical team the practical, actionable knowledge needed to meet the blueprint's demands effectively and pass the final inspection.
This difference is critical. Only ISO 27001 provides a path to certification, which has become an essential sales tool for building client trust and getting past grueling security questionnaires. The market clearly signals its importance; read more about the rise of ISO 27001 in Europe, where adoption has surged.
ISO 27001 vs ISO 27002 At A Glance
To make the roles of each standard perfectly clear, the table below breaks down their core attributes. Understanding this is the first step toward building a compliance program that actually helps you win deals, not just tick boxes.
| Attribute | ISO 27001 (The 'What') | ISO 27002 (The 'How') |
|---|---|---|
| Primary Purpose | Defines the requirements for establishing, maintaining, and improving an ISMS. | Provides detailed guidance and best practices for implementing security controls. |
| Certification | Certifiable. This is the standard you are audited and certified against to prove compliance. | Not certifiable. It is a supporting code of practice and an actionable implementation guide. |
| Scope | Covers the entire ISMS, including risk management, leadership, and continuous improvement. | Focuses specifically on the implementation details of information security controls. |
| Language | Uses mandatory language like "shall" to specify auditable requirements. | Uses advisory language like "should" to provide best-practice recommendations. |
| Audience | Management, compliance officers, and auditors who need to verify compliance. | Technical teams, security managers, and IT staff responsible for implementation. |
Ultimately, you can't achieve ISO 27001 certification without the wisdom of ISO 27002. They are two sides of the same coin, designed to work together to help you build a security posture that is both robust and fully auditable.
A Detailed Look At Each Standard's Structure

To truly grasp the relationship between ISO 27001 and ISO 27002, you have to look past high-level descriptions and dive into their architecture. For any technical leader at an SMB or startup tasked with building a secure environment, understanding these structures isn't just helpful—it's essential for a successful implementation.
ISO 27001 is built around mandatory clauses that form the foundation of your ISMS. ISO 27002, in contrast, is arranged thematically, acting as a comprehensive reference library of controls that provides the detailed "how-to."
The Prescriptive Framework of ISO 27001
The core of ISO 27001 is in Clauses 4 through 10. These are the mandatory requirements your organisation must meet to get certified. They provide the management framework for identifying, assessing, and treating information security risks.
Think of these clauses as the strategic pillars of your security program:
- Clause 4 (Context): Understand your business, stakeholders, and their security expectations.
- Clause 5 (Leadership): Get top management actively involved, defining roles and a clear security policy.
- Clause 6 (Planning): Systematically identify and assess risks, then create a concrete plan to treat them.
- Clause 7 (Support): Ensure you have the right resources—people, awareness, and documentation—to support the ISMS.
- Clause 8 (Operation): Execute your risk treatment plan and implement the security controls.
- Clause 9 (Performance Evaluation): Continuously monitor, measure, and audit your ISMS to see if it’s working.
- Clause 10 (Improvement): Learn from issues and nonconformities to make your ISMS stronger over time.
The language here is critical. ISO 27001 uses the word "shall," which means each point is a mandatory, auditable requirement.
The most telling difference is in the language. ISO 27001’s use of ‘shall’ creates non-negotiable requirements for building an ISMS. In contrast, ISO 27002 uses ‘should’ to provide actionable, best-practice recommendations for putting specific security controls in place.
The Thematic Control Library of ISO 27002
While ISO 27001 sets the management framework, its Annex A provides a list of potential security controls. The problem is, Annex A only gives a short description for each. This is where ISO 27002 becomes your indispensable implementation guide, offering a deep dive into how to actually build and run these controls.
The 2022 update to ISO 27002 organises its guidance into four practical themes:
- Organisational Controls: Foundational controls for policies, asset management, and third-party supplier security.
- People Controls: Focuses on the human element, from awareness training and background checks to secure remote working.
- Physical Controls: Guidance on securing offices, protecting equipment, and implementing clear desk/screen policies.
- Technological Controls: The technical core, covering access control, cryptography, network security, secure development, and more.
For every control in Annex A, ISO 27002 provides granular detail on its purpose, attributes, and specific implementation advice. This transforms a simple checklist into a practical user manual for your security and engineering teams. For a closer look, you can explore our detailed guide on ISO 27001 Annex A.
This structural difference is fundamental. ISO 27001 provides the governance framework; ISO 27002 provides the deep technical implementation guidance. One builds the house; the other shows you how to correctly install every lock, window, and alarm system.
How The Standards Work Together For Certification
Knowing the difference on paper is one thing, but the real test is seeing how ISO 27001 and ISO 27002 work together to get you certified. Let's be clear: your business is audited and certified against ISO 27001 only. There is no "ISO 27002 certification."
However, trying to pass an ISO 27001 audit without the detailed guidance from ISO 27002 is a recipe for failure. One standard sets the non-negotiable requirements, while the other provides the practical playbook. Together, they turn compliance from a theoretical goal into an audit-ready reality.
The Audit Process From A High Level
During an ISO 27001 certification audit, an external auditor will scrutinize your ISMS to confirm it meets every mandatory requirement in Clauses 4-10. They are looking for hard evidence that your system is planned, implemented, maintained, and continually improving.
A huge part of this involves the auditor examining two key documents:
- Risk Treatment Plan (RTP): This shows you have a systematic approach to risk. It details exactly how you plan to address the specific information security risks you've identified.
- Statement of Applicability (SoA): The SoA is your control inventory, listing every security control from Annex A. You must declare whether each is applicable, justify why or why not, and link it back to your risk assessment.
An auditor's job goes beyond just ticking boxes. They are there to confirm that the security controls you've chosen in your SoA are not only in place but are actually working effectively for your business and its unique risks.
ISO 27002 As Your Implementation Playbook
This is where the partnership between the two standards shines. Your SoA declares what controls you have, but the auditor will absolutely want to see how you’ve implemented them. This is where your team’s hard work, guided by ISO 27002, is put to the test.
Let's say your SoA states you've implemented control A.9.4.1, "Secure log-on procedures." That ticks the box for ISO 27001.
But the auditor’s next question will be, "Show me." They'll want to see your password policies, your multi-factor authentication (MFA) setup, and the documented procedures your employees follow. The detailed, practical guidance in ISO 27002 is what your team would have used to build those very systems. In short, the "how" from ISO 27002 becomes the auditable proof for the "what" in ISO 27001.
This dynamic applies across your entire ISMS. Whether drafting a teleworking policy or setting up rules for information transfer, ISO 27002 gives you the best-practice advice needed to build a control that's both effective and defensible in an audit. This synergy is key to a smooth certification. For a much deeper look, learn more about preparing for ISO 27001 audits in our comprehensive guide.
Answering Security Questionnaires and Winning Deals
For any SMB or startup, the sales cycle often hits a wall when a security questionnaire from a large prospect arrives. These documents are a major pain point—exhaustive, complex, and a standard roadblock in enterprise procurement. This is where understanding the ISO 27001 vs 27002 relationship becomes a powerful sales enablement tool.
An ISO 27001 certification acts as a universal trust signal. It tells enterprise clients your company takes security seriously and has a mature system to prove it. This certificate alone can satisfy a huge chunk of their due diligence, often leading to shorter questionnaires or bypassing them entirely.
But the certificate won't answer every specific query. This is where ISO 27002 becomes your secret weapon for crafting precise, evidence-backed responses that build real confidence and get deals over the line.
From High-Level Trust to Granular Proof
When a potential client asks, "How do you manage access control for sensitive systems?" simply saying "We are ISO 27001 certified" isn't enough. They want the specifics. They need to know how you actually implement the control. This is exactly what ISO 27002 provides: the detailed best practices your technical team used to build those very controls.
You can lean on ISO 27002's guidance to formulate answers that are technically correct and demonstrate a deep understanding of security principles. This allows you to articulate your security posture with authority, turning a tedious questionnaire into a chance to showcase your maturity.
Here's how they work together to accelerate sales:
- ISO 27001: Your certification is the "master key." It gets you through the door and satisfies the initial, high-level security requirement.
- ISO 27002: The detailed guidance is your "source material." It provides the script for answering specific, technical questions about how your controls are implemented daily.
A solid ISO 27001 certification often plays a crucial part when writing compelling business proposals, as it clearly demonstrates your commitment to information security and ticks a critical procurement box right from the start.
Accelerating Sales with AI-Powered Compliance
Manually cross-referencing hundreds of questionnaire items with your internal policies and ISO 27002's guidance is incredibly time-consuming. This is a massive pain point that pulls your best engineering and security minds away from their real jobs, grinding your sales team to a halt. This is the exact problem compliance automation platforms were built to solve.
For CTOs and InfoSec managers stuck dealing with these forms, the goal is efficiency and accuracy. While an ISO 27001 certificate proves you're committed, it’s the detailed guidance from ISO 27002 that informs the precise responses that get deals signed. Using a platform with a Smart Library can save up to 90% of the effort on these painful forms.
The real challenge for scaling businesses isn't just getting certified; it's operationalising that compliance. You need a way to instantly translate your verified security posture into the language of client questionnaires without grinding your sales and engineering teams to a halt.
This is where a platform like Compli.st becomes a strategic part of your sales process. By ingesting all your existing compliance evidence—audit reports, policies, control documentation—our platform builds an intelligent, centralized knowledge base.
When a new questionnaire arrives, our AI-powered system doesn't guess. It uses your own ISO 27001 evidence and ISO 27002-aligned control details to generate accurate, source-cited responses in minutes. Your sales team gets what they need instantly, your engineers stay focused on the product, and you close deals faster. It turns compliance from a defensive cost center into a proactive revenue driver.
Choosing The Right Approach For Your Business
Working out the difference between ISO 27001 and ISO 27002 isn't just a box-ticking exercise. It's a strategic decision that needs to align with your specific business goals, budget, and the pressures you're facing in the market. The right path really depends on where your organisation is at and what you need to achieve right now. This isn't about picking one standard over the other; it’s about deciding on the most sensible starting point for your compliance journey.
Your decision should be a direct answer to the problems you're trying to solve. Are you building a security programme from the ground up? Do you urgently need a formal certificate to get sales deals over the line? Or are you looking to fine-tune an already well-oiled machine? Each of these situations calls for a different way of using these powerful standards.
Scenario 1: For Startups Building A Security Foundation
If you're a startup or a small business just starting to get serious about your security posture, chasing full ISO 27001 certification can feel like a massive undertaking. Right now, your main headache isn't passing an audit; it's building a solid, practical security programme without getting bogged down in bureaucracy.
In this case, ISO 27002 is your best friend. Think of it as your foundational guide. It gives you a comprehensive library of best practices that you can put in place one step at a time. Instead of trying to do everything at once, you can focus on the high-impact areas first, like access control and asset management, using ISO 27002's detailed advice to build robust controls from day one. This approach creates a strong security baseline that sets you up perfectly for future certification when the time is right.
Scenario 2: For SMBs Facing Client Pressure
For many small and medium-sized businesses, the push for compliance comes from outside. A huge enterprise client sends over a security questionnaire, and it quickly becomes clear that ISO 27001 certification is a deal-breaker. The pain point here is immediate and very real: a blocked sales pipeline.
Here, your objective is crystal clear: achieve ISO 27001 certification. It's the non-negotiable goal. Your path involves using the full standard to set up a formal ISMS, concentrating on Clauses 4-10 to build the management framework itself. ISO 27002 then becomes your implementation manual for the controls you select in your Statement of Applicability (SoA), making sure they’re effective and ready for an auditor’s scrutiny.
This decision tree shows how certification can directly impact your ability to close deals after that dreaded security questionnaire lands.
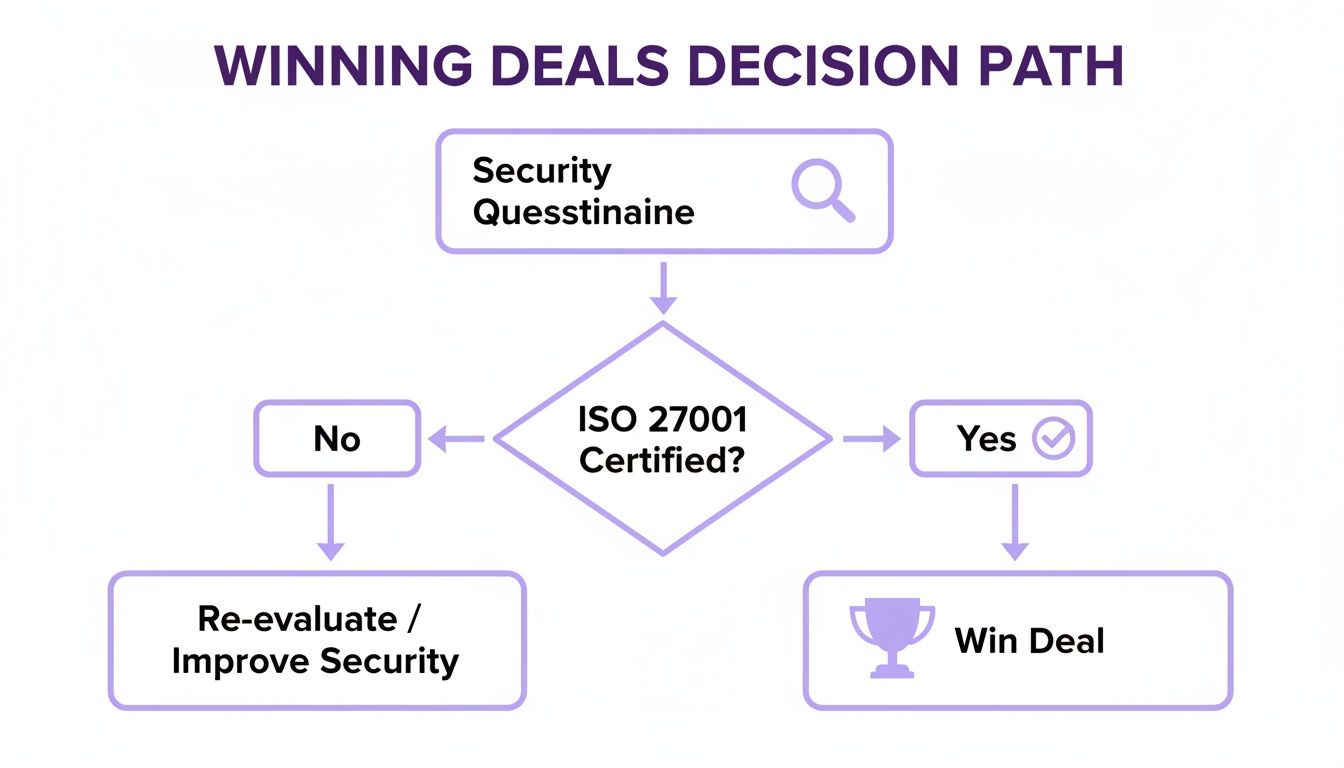
As the flowchart shows, holding an ISO 27001 certificate is often the quickest way to satisfy due diligence and keep a deal moving forward.
Scenario 3: For Mature Companies Refining Controls
If your organisation already has a mature ISMS—perhaps you're already certified or compliant with another framework—your needs are different. You aren't starting from scratch; you're looking to strengthen specific areas or tackle new risks, like those coming from cloud security or secure development.
For established companies, ISO 27002 serves as a tool for targeted improvement and continual refinement. It allows you to conduct deep dives into specific control areas without having to re-engineer your entire ISMS.
In this situation, ISO 27002 is used for surgical precision. You can use its detailed guidance to review and bolster individual controls. For instance, if you're worried about your incident response capabilities, you can turn to the relevant sections of ISO 27002 to benchmark your current processes against global best practices and spot where you can improve. The standard becomes a go-to resource for continuously optimising your security posture. For a deeper look at this process, you can explore more about risk management according to ISO 27005 in our related article.
Streamlining Your Compliance With Automation

Understanding the ISO 27002 vs 27001 dynamic is the first step. ISO 27001 gives you the auditable framework—the certificate that unblocks sales—while ISO 27002 provides the practical guidance for building a solid security program. But theory doesn't solve the biggest compliance pain point for SMBs: the sheer manual effort.
Manually collecting evidence, tracking risks in spreadsheets, and responding to endless security questionnaires is a massive resource drain. It pulls your best people away from innovation, turning compliance into a frustrating, reactive chore that slows down growth.
Beyond Manual Compliance Management
The real challenge isn't just getting certified; it's maintaining a strong security posture and proving it on demand without derailing your entire team. Manual processes are slow, error-prone, and don't scale. Every new client questionnaire forces you to drop everything and restart the painful cycle of digging for documents and writing responses.
This is where a purpose-built compliance automation platform makes a strategic difference. It helps you transform your security program from a one-off project into a living asset that actively supports your business.
The goal is to transform compliance from a defensive cost centre into a proactive revenue driver. This happens when you can instantly translate your verified security posture into the language of client questionnaires, without grinding your sales and engineering teams to a halt.
For companies aiming to efficiently manage their regulatory obligations, exploring how AI Chatbots to Improve Compliance with Regulations can offer powerful solutions. Automation is the key to tackling the most painful parts of the compliance journey head-on.
Turning Compliance Into A Business Accelerator
A platform like Compli.st was designed to solve these exact pain points for SMBs and startups. We automate the most demanding compliance tasks, mapping evidence and controls directly to both the formal requirements of ISO 27001 and the practical guidance of ISO 27002.
Here’s how we turn your compliance burden into a competitive advantage:
- Automated Evidence Collection: We connect to your tech stack to continuously pull proof that your controls are working, making audit prep far less painful.
- AI-Powered Questionnaire Responses: Our Smart Library uses your existing policies and evidence to generate accurate, source-cited answers to client security questionnaires in minutes, saving up to 90% of the effort.
- Streamlined Risk Management: Run ISO-aligned risk assessments, generate clear heatmaps, and build prioritized remediation plans without getting lost in spreadsheets.
- Build Client Trust: Use our public Trust Center to centralize your certifications and security documents, building confidence with prospects and reducing the number of inbound questionnaires.
By automating these processes, Compli.st helps turn your complex compliance project into a scalable business asset. It’s all about building trust, winning over enterprise clients, and giving your sales team the tools they need to close deals faster.
Frequently Asked Questions
When you're trying to get your arms around information security standards, a lot of practical questions come up. This is especially true when you're sorting out ISO 27001 vs ISO 27002. Here are a few of the most common things we hear from startups and growing businesses trying to build a solid compliance programme.
How Much Does ISO 27001 Certification Really Cost?
There's no single price tag for ISO 27001 certification. The cost really hinges on your company's size, the complexity of your operations, and how much security work you've already done. For a small or medium-sized business, you should plan for a few key expenses.
- Getting Ready (Consulting & Prep): This can be anything from a few thousand to tens of thousands of euros. It all depends on how much help you need from outside experts to get your ISMS in order.
- The Certification Audit: This is the main event—the official two-stage audit from an accredited body. You can expect this to be in the range of €10,000 to €25,000, sometimes more, for the initial three-year certification cycle.
- Keeping it Going: Don't forget about the ongoing costs. You'll have surveillance audits in the second and third years, plus the internal time and resources needed to keep the ISMS running and improving.
One way to manage these costs is by using compliance automation tools. They can often cut down on the need for expensive consultants, which helps ease the financial pressure.
How Long Does The Whole Implementation Take?
Just like the cost, the timeline for getting ISO 27001 certified can vary quite a bit. It really depends on your starting point. For most small to medium-sized businesses, a realistic timeframe is anywhere from six to twelve months.
This schedule is shaped by things like the scope of your ISMS, who you have available internally to work on it, and how bought-in your leadership team is. A project with dedicated resources and strong executive backing will always move faster.
How Do ISO 27001 and SOC 2 Fit Together?
People often ask about ISO 27001 and SOC 2. Both are highly credible security attestations, but they're built for different purposes and different audiences.
- ISO 27001 is the global benchmark for certifying your Information Security Management System (ISMS). It proves you have a structured, risk-based approach to managing information security. Its recognition is worldwide.
- SOC 2, on the other hand, is a framework mostly used in the US. It results in a report that describes your controls as they relate to specific "Trust Services Criteria" like Security, Availability, and Confidentiality.
Here's the core distinction: ISO 27001 certifies the entire management system—the "how" and "why" of your security programme. A SOC 2 report is an attestation from an auditor about how well your specific controls are actually working. Many companies end up getting both to meet the demands of a global client base.
Ready to stop wrestling with security questionnaires and start closing deals faster? See how Compli.st uses AI to automate your compliance, generate source-cited answers in minutes, and turn your security posture into a powerful sales tool. Learn more at https://www.compli.st.