ISO 27001 Annex A lays out 93 controls organised into 14 domains. Think of it as a blueprint for startups and SMBs, guiding you to pick security measures that reflect your unique risk posture. It streamlines decision-making when setting up your Information Security Management System (ISMS), while also dovetailing with NIS 2, DORA and SOC 2 Type 2 requirements.
Why ISO 27001 Annex A Matters
Many SMBs find themselves juggling overlapping controls, manual trackers and endless security questionnaires—only to discover unexpected audit gaps. Annex A steps in as a structured catalogue, matching safeguards directly to tangible threats and accelerating compliance across ISO 27001, NIS 2 and DORA.

Bringing Annex A into your ISMS design early takes the guesswork out of compliance and speeds up audits, vendor RFPs and security questionnaires. The result? A clearer Statement of Applicability, leaner processes and fewer surprises when regulators or customers knock on your door.
- Simplify control selection based on risk assessments
- Centralise evidence to avoid audit gaps
- Automate evidence tracking and security questionnaires with Compli.st
- Accelerate NIS 2 and DORA readiness side-by-side with ISO 27001
- Improve your risk posture and regulatory readiness in record time
Common Pain Points
Outdated spreadsheets turn control tracking into a maze. Teams juggle silos of policies, scattered logs and endless questionnaire follow-ups.
Use Annex A as your control menu to cut through complexity and defend your assets—without drowning in manual work.
Platforms like Compli.st ingest policies and evidence, auto-populating your SoA entries and vendor questionnaire responses. That slashes manual work, speeds audits and keeps customers happy.
Tailoring Annex A To Your Risks
Begin with a thorough risk assessment and map each threat to the relevant Annex A control. Focus only on what truly matters:
- Map each identified risk to its control identifier in Annex A
- Exclude non-relevant controls and document your rationale in the SoA
- Use digital tools to track control status, evidence and questionnaire answers in real time
Once you’re aligned, dive into each domain and roll out controls that align perfectly with ISO requirements and complementary frameworks like NIS 2 and DORA.
How Compli.st Accelerates Compliance
Compli.st taps into your policy library, past audit reports and customer questionnaires to auto-generate control evidence and responses. You’ll answer vendor and regulator queries in minutes, complete with source-cited references.
- Import existing audit reports for instant SoA updates
- Automate NIS 2 and DORA crosswalks alongside Annex A mappings
- Produce audit-ready reports and security questionnaire responses with just a few clicks
By combining Annex A’s clear structure with Compli.st’s automation, you transform a once-daunting compliance journey into a smooth, predictable process.
Understanding Core Principles And The PDCA Cycle
Think of your ISMS as a living organism, constantly adapting to external pressures and internal shifts. Policies are its backbone, processes act like organs—and continuous improvement is the heartbeat that keeps you ahead of threats.
- Policies set the rules that guide secure behaviour.
- Processes perform essential tasks, from data classification to incident response.
- Continuous improvement keeps the system agile and responsive.
This metaphor highlights why controls must blend into everyday workflows. The ISO 27001 Annex A catalogue offers a clear menu of controls, each slotting neatly into these roles.
Implementing Plan Do Check Act
The PDCA cycle breaks implementation into manageable stages:
- Plan
Start with a risk assessment to pinpoint the threats that matter most. - Do
Roll out chosen Annex A controls with designated owners, clear documentation and sufficient resources. - Check
Monitor performance using metrics, tests and regular reviews. - Act
Close gaps, adjust policies and sharpen controls based on what you learn.
A typical sequence might look like this:
- Identify and analyse risks against business objectives
- Select Annex A controls on the basis of impact and feasibility
- Document responsibilities, timelines and resource needs
- Execute controls and collect initial evidence
- Review outcomes and update your Statement of Applicability
Relating Controls To Risk And SoA
Your risk assessment steers which Annex A controls take priority. The Statement of Applicability (SoA) then becomes your control roadmap—detailing why you included or excluded each measure.
A clear, evidence-backed SoA demonstrates intentional decision-making to auditors.
Early-stage teams often focus on controls such as A.8.2 (data classification) and A.16.1 (incident response). A tool like Compli.st can automate mappings, curate audit-ready evidence and integrate crosswalks to SOC 2 Type 2, NIS 2 and DORA:
- Automated evidence collection cuts manual logs by 50%
- Real-time SoA updates enhance compliance visibility
- Source-cited answers slash vendor questionnaire time by 90%
With that foundation, you’re ready to tackle deeper control domains and structured roll-outs.
Documenting Evidence And Ownership
Turning each control into a living, breathing process hinges on clear accountability. Assign a single owner per control to maintain visibility and drive proactive management.
- Assign an owner for every control to track accountability and outcomes
- Gather diverse evidence—policy documents, system configs and test logs
- Keep version histories and timestamps to support audit trails
Link artefacts directly to control IDs and watch audit prep accelerate—often by 40%. Regular reviews in the Act phase ensure your approach stays aligned with real-world results.
Armed with these principles, you can confidently apply Annex A across your organisation. In the next section, we’ll explore how ISO 27001 Annex A splits controls into 14 domains, from asset management to supplier relationships, and show how layering these domains builds a defence-in-depth strategy that minimises fatigue and stretches resources further.
Ready to drive change.
Exploring Control Domains And Structure
When you dive into ISO 27001 Annex A, you’ll find 93 controls neatly organised into 14 domains—imagine them as overlapping shields protecting a stronghold. Each domain zeroes in on a specific security concern, from managing digital keys to ensuring only authorised users gain access.
- Organisational Security Policies: Set clear rules and acceptable behaviour.
- Asset Management: Keep a precise inventory of hardware, software and data.
- Access Control: Enforce least-privilege and manage user permissions.
- Cryptography: Safeguard information both in transit and at rest.
- Supplier Relationships: Monitor third-party risk and contractual obligations.
- Change Management: Introduce updates without opening new vulnerabilities.
- Incident Management: Detect anomalies quickly and coordinate response.
- Physical Security: Protect your facilities, servers and tangible assets.
Each of these layers works in concert, framing a robust defence strategy.
Layered Defence Analogy
Think of your security posture as a castle. Solid walls—preventive controls—keep attackers at bay. Sensors—detective measures—spot intruders, while gates—corrective actions—guide threats back under control.
A layered approach ensures no single gap exposes your entire fortress.
In practice, a SaaS startup might pour resources into Cryptography and Access Control, whereas a consultancy could focus on Asset Management and Supplier Relationships to shield client information.
Spotting Priority Zones
Not every organisation has infinite time or budget. That’s why small and medium businesses should align domain efforts with their risk profile and resource availability. This targeted focus helps teams funnel energy where it matters most.
- Score each domain by potential impact and likelihood.
- Pinpoint top-risk controls and tackle those first.
- Assign clear ownership and schedule regular reviews.
- Re-evaluate priorities quarterly as new threats surface.
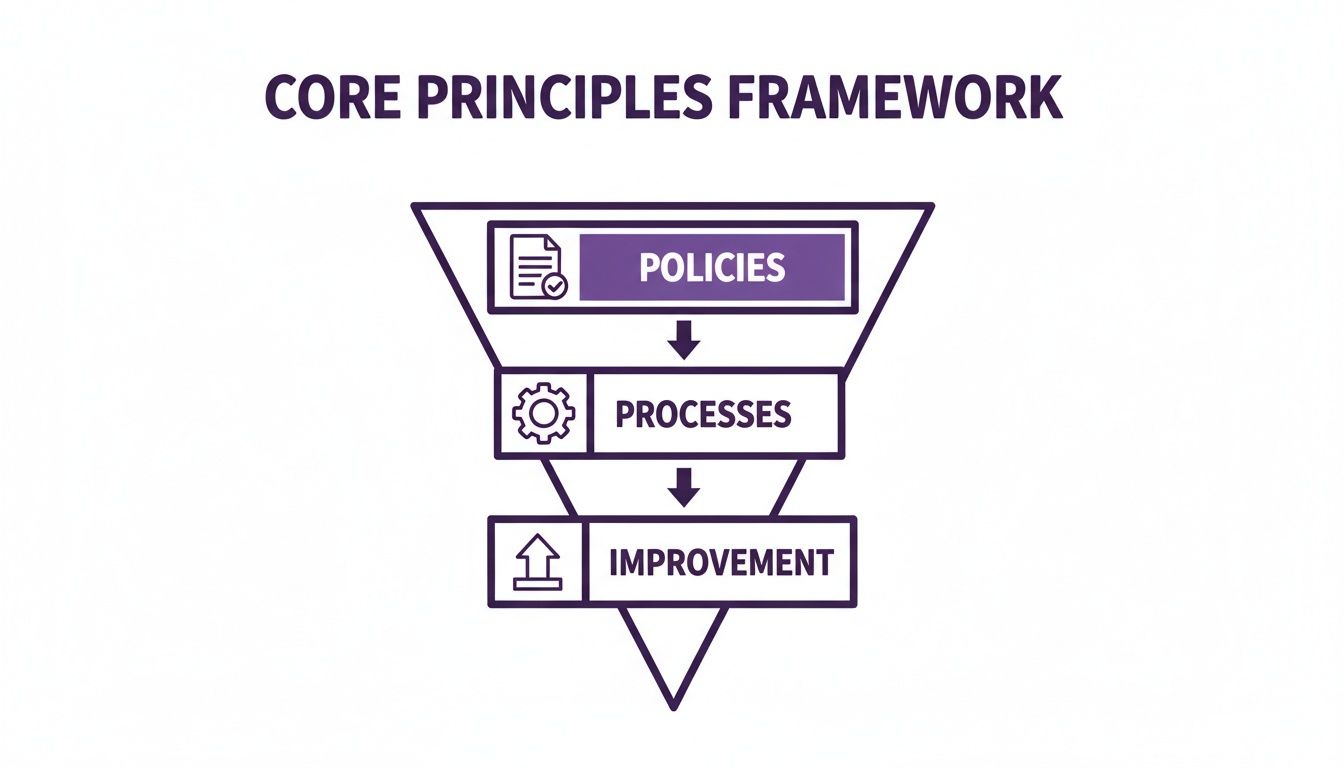
This visual highlights how policies form the base, processes drive execution and improvement pushes maturity upward.
You might be interested in our guide on GDPR register management to see how control mapping supports privacy compliance.
Leveraging Compli.st For Evidence
Manually gathering evidence across folders, spreadsheets and emails slows you down—and auditors notice. Compli.st centralises proof points, linking artefacts directly to Annex A requirements, NIS 2 and DORA controls, slashing questionnaire time by 90%.
- Store policies, logs and test records in one secure platform
- Automatically generate your Statement of Applicability (SoA)
- Track updates, review deadlines and audit trails in real time
With evidence in hand and dependencies mapped, you stay audit-ready without frantic last-minute scrambles.
Next Steps And Focus Areas
- Conduct a domain gap analysis to chart existing controls
- Prioritise high-impact domains for your first implementation sprint
- Use Compli.st to auto-generate evidence and maintain your SoA
- Schedule quarterly domain reviews to adapt to evolving risks
A clear domain map turns Annex A from a tick-box exercise into a strategic defence plan.
Effective layering of controls is the key to robust information security.
Domain Spotlights
Access Control sits on the frontline, defining who can step inside digital and physical boundaries. Implement multi-factor authentication, enforce least-privilege roles and set session timeouts to thwart unauthorised entry.
Supplier Relationships often harbour hidden threats when third parties lack adequate safeguards. Run thorough due-diligence questionnaires and maintain ongoing monitoring—Compli.st’s automation streamlines this process.
Quick Tips
- Review Cryptography policies and rotate keys on a regular schedule
- Conduct realistic Incident Response drills at least twice a year
By concentrating on these targeted controls, you’ll allocate resources wisely, build continuous security maturity and adapt seamlessly as new challenges emerge.
Reviewing Key Changes And Control Comparison
The 2022 update to ISO 27001 Annex A feels like pruning a garden—outdated branches have been removed so fresh growth can flourish. Controls have slimmed down from 114 to 93, merging overlaps and retiring entries that no longer reflect today’s threat environment.
That shift sharpens focus on cloud security, threat intelligence and supply-chain risks. Auditors will notice fewer redundancies, making prep smoother and more targeted.
- 21 fewer controls through smart mergers and removals
- 11 new controls addressing cloud use, ongoing threat analysis and secure coding
- Simplified domains that cut complexity for CISOs and implementation teams
By mapping your existing framework to the revised catalogue, you avoid starting from scratch. For instance, the new A.5.7 on Threat Intelligence turns one-off reports into a continuous monitoring practice.
Comparison Of Annex A Controls Between Versions
Below is a quick overview of how the control set has evolved between editions. It highlights the total count, fresh entries and core adjustments.
| 2013 Version | 2022 Version | Key Changes |
|---|---|---|
| 114 controls | 93 controls | Merged overlaps and removed obsolete entries |
| No cloud-specific control | A.5.23 Cloud Service Use | Introduces formal cloud security requirements |
| No dedicated TI control | A.5.7 Threat Intelligence | Embeds real-time threat collection and analysis |
This snapshot makes it easier to plan your shift from the 2013 structure to the updated layout.
Mapping Controls From 2013 To 2022
Think of mapping as creating a translation guide. You list each 2013 control ID next to its 2022 counterpart in your Statement of Applicability. Keep a record of any renamed or merged entries so you can trace audit evidence back to the original clauses.
In practice:
- Build a simple spreadsheet with old and new IDs
- Note any scope changes (for example, when encryption controls were consolidated)
- Attach cross-references in your audit logs to maintain clarity
This diagram shows how Annex A slots under Clauses 4 to 10, grouping controls into thematic clusters.
Interestingly, France saw a 44% jump in ISO 27001 certifications post-2022, compared with a 19% rise globally. Learn more about ISO 27001 adoption trends in France.
Key Rationale Behind Version Changes
Dropping redundant controls is like decluttering a workspace—teams focus on what truly matters. Here are the standout updates:
- Threat Intelligence (A.5.7): Moves beyond annual reports to continuous threat feeds.
- Cloud Service Use (A.5.23): Establishes clear security guardrails for cloud deployments.
- Secure Coding (A.8.28): Embeds vulnerability checks directly into development workflows.
These additions reflect real-world attack patterns and help you align your ISMS with current risks.
Planning Your Update Path
Begin with a gap analysis between your existing SoA and the 2022 Annex A. Then break the work into manageable sprints—think of each control as a checkpoint on your marathon rather than a single giant leap.
High-priority milestones might include:
- Assigning control owners for new and merged entries
- Revising policy documents to reference updated control IDs
- Running pilot tests on critical items, such as secure coding practices (A.8.28)
Regular reviews—ideally quarterly—keep everyone on track and adaptable to new threat intelligence.
Updated controls in Annex A sharpen focus on real risks and ease your audit journey.
Next Steps For Compliance
- Conduct a fresh risk assessment against the 2022 Annex A.
- Refresh your Statement of Applicability, marking new and consolidated controls.
- Train staff on the new requirements, aiming for 90%+ awareness within three months.
A platform like Compli.st can automate control mapping, evidence gathering and report generation. Many teams cut questionnaire time by 90% and keep proof centrally cited for auditors.
By following these steps, your organisation gains stronger resilience and a smoother audit experience. Set monthly milestones, track metrics like incident response times and staff training rates, and you’ll turn the update into a structured, predictable process. Happy auditing!
Aligning Controls With Risk Assessment And Statement Of Applicability
When selecting ISO 27001 Annex A controls, let your risk treatment strategy lead the way. Only those controls that tackle your actual risks earn a spot. These choices flow directly into your Statement of Applicability (SoA), smoothing the path for any audit.
Steps To Align Controls With Risk
To map each risk to Annex A controls, follow a clear five-step workflow:
- Gather your risks along with context and likelihood ratings.
- Match each risk to the relevant Annex A controls based on your treatment decisions.
- Record whether you include or exclude a control, and link it to evidence.
- Draft SoA entries with concise justifications for each decision.
- Review and obtain stakeholder approval before finalising.
For instance, a potential data breach might map to A.8.2 (asset classification) and A.10.1 (encryption). Tools like Compli.st can automate this mapping, storing source-cited evidence for every entry.
Drafting Statement Of Applicability
Think of the SoA as your compliance roadmap. It shows which ISO 27001 Annex A controls you apply—and why. Every line needs three elements:
- A control identifier exactly as it appears in Annex A
- The inclusion status (Yes/No)
- A clear rationale for your choice
Best practices include:
- Linking each control to its corresponding policy or technical procedure
- Explaining any exclusions by citing risk acceptance or transfer
- Timestamping decisions and tracking owner approvals
Compli.st can generate a draft SoA in minutes by pulling evidence from your Smart Library.
Startup Scenarios For Control Selection
Small, agile organisations often juggle tight budgets and big risks. Imagine a lean SaaS team facing backup failures and data-breach threats.
A concise SoA shows auditors you made control choices based on real risks, not checkbox tokenism.
| Risk | Control ID | Rationale |
|---|---|---|
| Backup failure | A.12.3 | Ensures regular restore tests |
| Data breach | A.10.1 | Encryption of sensitive assets |
Mapping your top risks to Annex A controls builds a transparent audit trail and guides remediation.
- Schedule quarterly SoA reviews tied to updated risk assessments
- Sync evidence attachments whenever policies change
- Store audit comments and corrective actions in your compliance centre
Implementing this approach with Compli.st can cut mapping time by 90%, keeping your SoA aligned with ISO 27001 Annex A and demonstrating deliberate, risk-based control selection. Finally, set recurring reminders for risk updates and SoA adjustments to close the loop on continuous improvement.
Maintaining Audit Evidence And Continuous Review
An auditor won’t accept vague statements—they want proof. Use a central repository to attach logs, screenshots and policy excerpts directly to each SoA entry.
- Label evidence with date and version details
- Archive test results and incident reports in one place
Compli.st tracks every attachment change, creating an audit log that inspectors respect. By scheduling periodic reviews, you make sure controls stay relevant as your business evolves.
Continuous evidence management turns compliance from a reactive chore into proactive governance.
Next Steps For Audit Preparedness
Your draft SoA now needs final validation from leadership and the risk committee. Circulate it internally, gather feedback on excluded controls and ensure your evidence is rock-solid.
- Confirm each control status matches your treatment decisions
- Secure stakeholder sign-off on the final Statement of Applicability
With Compli.st, you can generate sign-off records and export the SoA as a PDF complete with embedded evidence references. This closes the loop between risk assessment, control selection and documented justification—ready for audit or client review.
Start applying these methods today to keep your ISO 27001 Annex A implementation transparent, consistent and defensible.
Ready for audit.
Implementing Controls And Audit Evidence With Compli.st

Getting Annex A controls off the ground often falters at policy drafting, evidence gathering and security questionnaire responses. Compli.st’s Smart Library centralises your procedures, ownership details and audit trail, so nothing slips through the cracks.
- Draft clear policy statements with ownership details and approval dates.
- Use built-in templates to accelerate policy creation and ensure completeness.
- Automate vendor and regulator questionnaire answers from your evidence store.
- Assign a responsible individual for each control to maintain accountability.
Assigning Roles And Responsibilities
Accountability hinges on defined roles. In Compli.st, you map each task back to your organisation chart, so there’s never a question of who does what.
- Control Owner drafts policies, updates evidence and assigns tasks.
- Tester runs validations and records outcomes.
- Auditor Reviewer checks submissions and approves SoA entries.
This clear-cut matrix cuts audit queries by 40% when every action carries a timestamp.
| Role | Responsibility |
|---|---|
| Control Owner | Draft policies, assign tasks and maintain evidence |
| Tester | Run control tests, capture logs and screenshots |
| Auditor Reviewer | Review submissions and confirm compliance status |
Tie these roles to automated alerts in Compli.st. Email reminders and live dashboards keep your team on track and prevent review bottlenecks.
Running Control Tests
With policies in place, you need proof that controls work. Compli.st walks you through each test step and captures results in real time. Reminders pop up before quarterly reviews, so nothing is ever overdue.
- Select the control test in your dashboard and assign testers.
- Execute test steps and upload evidence such as screenshots or sign-off forms.
- Review outcomes, log failures and trigger corrective actions immediately.
Auditors value consistent test logs tied to control IDs for faster approvals.
Logging Audit Evidence
A well-organised evidence folder impresses examiners and slashes back-and-forth. Compli.st links documents, version histories and timestamped notes directly to each control.
- Export system configurations to demonstrate technical settings.
- Store drill reports capturing incident scenarios with success metrics.
- Archive policy snapshots showing approved versions and review timestamps.
You might be interested in how ISO 27001 aligns with SOC 2 Type 2 in our guide on SOC Type 2 integration Check out our SOC 2 Type 2 guide.
Within Compli.st, continuity plans connect directly to live system inventories and stakeholder assignments. This transparency keeps teams aligned and shows auditors your end-to-end resilience management.
Information Security Continuity Spotlight
Control A.17 in Annex A focuses on information security continuity. In France, it requires planning, implementation, testing and PDCA-aligned review to build real resilience.
ANSSI logged over 1,200 significant cyber incidents in 2022, underlining the need for robust continuity measures. Certified organisations must document plans at all management levels, following PDCA:
- Plan risk-based strategies
- Do implement redundancies
- Check test via drills targeting 95% recovery success
- Act improve based on lessons learned
Learn more about ISO 27001 continuity insights in France
According to consultants like Factocert in Bordeaux, adopters of Annex A.17 see 35% faster recovery times. Broader benchmarks show downtime reductions of 28% for ISO 27001 certified entities in France thanks to these continuity controls.
Compli.st logs drill frequencies, verification records and recovery metrics so you can share key data with auditors in seconds.
- Schedule continuity drills at least quarterly within the platform.
- Set up dashboards to monitor recovery metrics and test coverage.
- Link corrective actions and post-drill findings to evidence entries for a seamless audit trail.
- Monitor test coverage with interactive charts in Compli.st.
By automating policy drafting, control testing and evidence management with Compli.st, you accelerate audits and bolster security continuity. Each control remains audit-ready around the clock.
Explore Compli.st features for a frictionless Annex A rollout. Next, discover common challenges and framework crosswalks in our final section.
Common Challenges And Framework Crosswalks
Treating ISO 27001 Annex A as nothing more than a tick-box exercise often means skipping the underlying rationale for each control. Teams rush through and then find themselves scrambling for evidence when auditors knock on the door.
As a result, documentation grows stale, gaps appear, and clarification requests pile up—just when you need a smooth audit. Integrating NIS 2, DORA and SOC 2 crosswalks at the same time can feel overwhelming without the right platform.
Common Missteps
- Skipping control rationales and leaving auditors in the dark.
- Letting evidence reviews slide, so artefacts become outdated.
- Overlooking overlaps between ISO 27001, SOC 2, NIS 2 and DORA, which multiplies effort instead of maximising value.
“Treat crosswalks as living documents; they reduce fatigue and speed auditor sign-off.”
Control Mapping Table
Below is a quick view of how Annex A controls map across SOC 2 and the GDPR. You can extend this table to include NIS 2 Articles and DORA requirements in Compli.st’s crosswalk module.
| ISO 27001 Annex A | SOC 2 Control | GDPR Article |
|---|---|---|
| A.9 User Access Management | CC6 Logical Access Control | Art 32 Security of Processing |
| A.7 Human Resource Security | CC3 Personnel Security | Art 24 Controller Responsibility |
| A.12 Operational Procedures | CC5 Change Management | Art 30 Records of Processing |
Mapping these equivalents helps you recycle evidence and slash questionnaire time by 70%.
Best Practices
- Begin with a gap analysis that ties each Annex A item back to your risk treatment plan.
- Adopt a centralised platform to auto-link evidence, control IDs and crosswalks across frameworks.
- Update your Statement of Applicability with overlaps and unique requirements.
- Schedule quarterly reviews so your crosswalks evolve alongside new regulations.
Learn more about five best Vanta alternatives to reduce vendor fatigue.
By aligning ISO 27001 Annex A with SOC 2, NIS 2, DORA and the GDPR, you forge a unified compliance strategy that shortens audit windows and earns stakeholder trust.
Example Use Case
A growing SaaS startup was drowning in siloed controls and separate framework mappings. Within days, the team centralised all policies in Compli.st and mapped 93 Annex A items to 25 SOC 2 controls, 10 NIS 2 Articles and 15 GDPR requirements.
Automatic evidence links and questionnaire templates popped into place. Audit readiness climbed from 60% to 95% in under two weeks.
Now, quarterly reviews take one hour instead of a full day. No more compliance hiccups derailing product roadmaps.
Sustained Alignment Tips
- Automate reminders for evidence refreshes to catch expired proofs.
- Version-control your crosswalk so you can trace how controls evolve.
- Assign framework champions who update mappings whenever regulations shift.
Stick to these habits, and your compliance engine will hum along smoothly.
Ready to simplify multi-framework compliance?