A SOC 2 Type 2 report isn't just a technical checkbox; it's the gold standard for proving your company handles customer data securely over the long haul. For a growing SMB or startup, think of it less as a compliance chore and more as a powerful sales asset that unlocks enterprise deals and builds the unshakeable trust you need to scale.
What a SOC 2 Type 2 Report Really Means for Your Business

If you're trying to land bigger customers, you've definitely seen "SOC 2" pop up on a daunting security questionnaire or during a high-stakes sales call. It feels like another hurdle, but its true value is what it signals to your customers: you don’t just say you’re secure, you have proven it over a meaningful period.
This report is the final output of a deep-dive audit by an independent CPA firm. They don't just look at your policies; they scrutinize your security controls in action over 3 to 12 months, verifying they work consistently in the real world.
From Claiming Security to Proving It
Let’s use an analogy. Imagine a car manufacturer saying their vehicle has top-tier safety features versus them providing a detailed, multi-month crash test report from an independent agency. The first is a marketing claim; the second is verified proof. A SOC 2 Type 2 report does the same thing for your company's data security.
- Claiming Security: Your website promises you encrypt data. You assure potential customers that your team follows security best practices.
- Proving Security: An independent auditor has tested your encryption controls for months and confirmed they operate exactly as designed. They’ve reviewed concrete evidence that your team is properly trained and consistently adheres to documented security procedures.
This leap from a simple assertion to a formal attestation is what gives the report its power. It offers customers tangible assurance that your systems aren't just well-designed on paper—they work effectively, day in and day out.
A SOC 2 report moves your business from 'claiming security' to 'proving security,' transforming a compliance hurdle into a competitive advantage that accelerates sales and builds lasting customer trust.
A Powerful Asset for Growth
For startups and SMBs, achieving SOC 2 Type 2 compliance is a major milestone that directly boosts the bottom line. This isn't just about playing defense against data breaches; it's about actively enabling growth. The report serves several vital functions:
- Unlocking Enterprise Deals: Many large organizations won't even consider a partnership without a SOC 2 report. It's often a non-negotiable.
- Answering Security Questionnaires: It proactively answers hundreds of questions that would otherwise tie up your engineering and sales teams for weeks.
- Building Credibility: It showcases a level of security maturity that immediately sets you apart from less established competitors in the market.
Ultimately, a SOC 2 Type 2 report is a strategic investment. It reframes security from a defensive cost center into a proactive tool for building trust, closing bigger deals faster, and scaling your business with confidence.
SOC 2 Type 1 vs Type 2: Which Report Do You Need?
Figuring out whether to get a SOC 2 Type 1 or a SOC 2 Type 2 report is a critical decision for any growing company. This isn't just an internal compliance choice; it directly impacts your timeline, budget, and most importantly, your sales conversations. Getting it wrong means stalled deals or wasted effort—something no startup or SMB can afford.
Let's use a simple analogy to clear things up. Imagine you're building a highly secure vault to protect priceless treasures.
A SOC 2 Type 1 report is like the architect's blueprint. It's a detailed plan showing that you’ve designed a vault with a strong door, reinforced walls, and a state-of-the-art alarm system. An inspector comes in on a single day, reviews the plans, and confirms the design is sound on paper.
A SOC 2 Type 2 report, on the other hand, is like having a security expert monitor that vault for six months straight. They’re not just looking at the blueprint; they’re actively testing the locks, checking for cracks in the walls after a storm, and making sure the alarm actually goes off during a simulated break-in.
The blueprint (Type 1) shows you have a good plan. The long-term monitoring (Type 2) proves your vault is genuinely secure in the real world, day in and day out.
SOC 2 Type 1 vs Type 2: A Head-to-Head Comparison
This table breaks down the fundamental differences between Type 1 and Type 2 reports to help you choose the right audit for your business needs.
| Attribute | SOC 2 Type 1 Report | SOC 2 Type 2 Report |
|---|---|---|
| Audit Scope | Tests the design of your security controls at a single point in time. It asks, "Are your controls designed correctly?" | Tests both the design and the operational effectiveness of controls over a period, typically 3-12 months. It asks, "Do your controls actually work consistently?" |
| Duration | The audit is a "point-in-time" snapshot. The entire process, including readiness, can be wrapped up in 2-4 months. | The audit requires an "observation period" of 3-12 months. The full journey often takes 9-15 months from start to finish. |
| Level of Assurance | Provides moderate assurance. It confirms you have a solid security plan but doesn't prove it works in practice over time. | Provides the highest level of assurance. It's the gold standard that enterprise clients and regulated industries demand as proof of ongoing security. |
| Cost | Less expensive upfront. Audit fees are generally lower because of the reduced scope and time commitment from the auditor. | More expensive. The extended observation period and deeper testing require a more significant investment in both auditor fees and internal resources. |
| Customer Perception | Seen as a good first step, but it might not be enough to satisfy demanding vendor security reviews, especially from larger clients. | Widely accepted as the definitive proof of security maturity, helping to speed up sales cycles and bypass lengthy security questionnaires. |
So, what's the verdict? A Type 1 report is a perfectly good way to show your initial commitment to security, and it's certainly faster. However, if your goal is to land those big enterprise deals, you should be planning for a SOC 2 Type 2. It’s a bigger investment, for sure, but the payoff in customer trust and unlocked revenue is more than worth it.
Understanding the Five Trust Services Criteria
Think of the SOC 2 framework less like a rigid rulebook and more like a set of guiding principles. At its core are the Trust Services Criteria (TSC), which represent five distinct promises you can make to your customers about how you handle their data. The key to a successful audit is choosing the criteria that truly reflect your business operations and the commitments you've made in client contracts.
Getting this selection right is critical. If you over-scope, you'll burn time and money implementing controls for promises you don't even make. But if you under-scope, your final report might not be enough to satisfy a key prospect, potentially derailing a major deal. The framework is designed to be adaptable, ensuring your audit is a genuine reflection of your service commitments.
The Foundation: Security
The Security criterion is the bedrock of every single soc type 2 audit. It's mandatory, and for good reason. Often called the Common Criteria, it covers the foundational controls that protect your entire system from unauthorized access, whether that’s a hacker trying to get in remotely or someone trying to walk out with a server.
It's the broadest of the five criteria, touching on essential practices like:
- Access Controls: Do you have strong password policies, multi-factor authentication, and role-based permissions to ensure only the right people can access sensitive information?
- Change Management: Is there a formal process for deploying changes to your production environment to prevent service disruptions or new security holes?
- Incident Response: When something goes wrong—a data breach, a system outage—do you have a documented plan to detect it, respond swiftly, and recover?
In short, the Security TSC proves you've built the basic defenses needed to protect customer data. Without this solid foundation, the other criteria wouldn't hold much weight.
Choosing Your Additional Criteria
Once you have Security covered, you can select from the other four criteria. This is where you really tailor the audit to your business. The guiding question should always be: "What have we promised our customers, and what are their biggest concerns?"
Availability
Do your customer contracts guarantee a certain level of uptime? If your Service Level Agreement (SLA) promises 99.9% availability, then the Availability criterion is a must-have. It shows auditors and customers that you have the right controls in place to meet that operational promise and keep your service accessible when they need it.
A perfect example is a cloud-based project management tool. If that platform goes down, thousands of teams are brought to a standstill. Including Availability in their soc type 2 report proves they have robust disaster recovery plans, performance monitoring, and backup systems ready to go.
Processing Integrity
You'll want to select Processing Integrity if your service involves any kind of complex calculation, transaction, or data manipulation where accuracy is everything. This criterion confirms that your system does its job completely and accurately—without errors, delays, or unauthorized changes.
Imagine a payroll processing platform or a financial analytics tool. Their clients' entire businesses rely on the numbers being right. This TSC validates the controls you have around data input, your system's processing logic, and output verification, giving customers confidence that the results are reliable, timely, and correct.
Scoping your SOC 2 audit correctly is all about alignment. Match the Trust Services Criteria you select with the explicit promises you make to your customers. This focus prevents wasted effort and delivers a report that directly addresses client concerns.
Confidentiality
The Confidentiality criterion is for any business handling sensitive information that needs to be kept under lock and key. This goes a step beyond general security to cover data that is specifically marked as confidential and requires strict protection from disclosure.
For example, a legal tech firm storing sensitive case files or a market research company handling proprietary corporate data would absolutely need this TSC. It demonstrates they have specific controls, like data encryption and rigorous access policies, to protect that information from the moment it enters their system until it’s destroyed, ensuring it's only ever seen by authorized individuals. For clients entrusting you with their most valuable data, this is non-negotiable.
A Step-by-Step Guide to the SOC 2 Type 2 Audit Process
The road to a SOC 2 Type 2 report can feel overwhelming, particularly for growing businesses juggling tight resources. But treating it like any other major project—with a clear, structured plan—is the key to success. A methodical approach doesn't just make it manageable; it prevents the costly delays that can bring critical sales deals to a grinding halt.
Think of it like building a house. You wouldn't just start laying bricks without a detailed blueprint and a solid foundation. In the same way, a successful audit depends on careful planning and prep work long before the official observation period kicks off. The entire journey breaks down neatly into four key phases.
Phase 1: Scoping and Gap Analysis
This is your strategic planning stage. Before an auditor can even begin, you need to define exactly what they’ll be looking at. This means choosing the right Trust Services Criteria—the principles that align with the promises you make to your customers about their data.
With the scope set, you move on to a gap analysis or readiness assessment. This is essentially a practice run. You’ll compare your current security controls against the SOC 2 requirements to see where you fall short. The goal is to create a clear roadmap for remediation, identifying every missing policy, procedure, or technical control before the clock on the formal audit starts ticking.
Phase 2: Readiness and Remediation
Now that you have your roadmap, it's time to get to work. The readiness phase is where you roll up your sleeves and implement the necessary controls. This is often the most time-consuming part of the whole process, typically taking 3-6 months.
During this stage, your team will be heads-down on tasks like:
- Writing and finalising policies: Documenting everything from your incident response plan to your access control policies.
- Implementing new tools: Deploying systems for things like endpoint security, vulnerability scanning, or security awareness training.
- Configuring systems: Making sure your cloud infrastructure and applications are set up according to security best practices.
A classic mistake, especially for smaller businesses, is underestimating the effort required here. If you don't properly fix the gaps you found in Phase 1, you're just setting yourself up for failure during the formal audit.
This infographic shows the five Trust Services Criteria, which form the core of any SOC 2 audit.
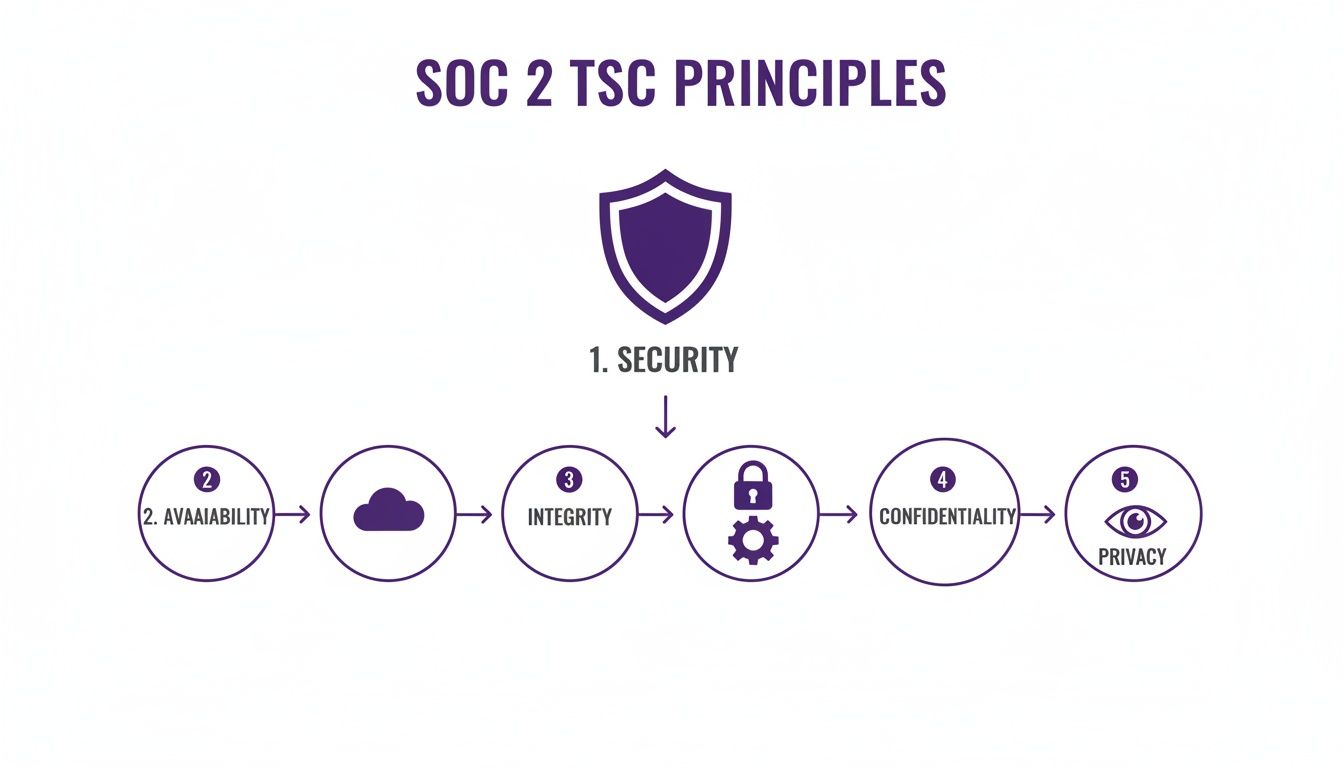
As you can see, Security is the mandatory foundation. You then add the other criteria based on the specific services and promises your business offers.
Phase 3: The Observation Period
This is the main event. For a period of 3 to 12 months, your chosen independent auditor will actively test your controls. They aren’t just looking at whether you have controls; they're verifying that those controls are actually working effectively over time.
This isn't a one-time spot check. The auditor will request evidence samples from different points throughout the period. For instance, they might ask to see new hire checklists from month one, access review logs from month three, and change management tickets from month five. Consistent evidence collection is everything—a single missing screenshot can lead to an audit exception.
The biggest challenge during the observation period is maintaining consistency. A control that works perfectly for five months but fails in the sixth is still a failed control in the eyes of an auditor.
Phase 4: Reporting and Attestation
Once the observation period ends, the auditor gets to work compiling their findings into the final SOC 2 Type 2 report. This is a comprehensive document that breaks down into four main sections:
- Management's Assertion: A formal letter from your company's leadership confirming that the description of your systems is accurate and the controls are suitable.
- The Independent Auditor's Report: This is the auditor's professional opinion on whether your controls were effective throughout the period.
- System Description: A detailed overview of your company's services, infrastructure, software, people, and processes.
- Control Tests and Results: A breakdown of every single control tested, the methods the auditor used, and the outcome of those tests.
Receiving an "unqualified opinion"—the best possible outcome—means you've passed. You'll have a powerful attestation of your security posture, ready to share with prospects and customers to build trust and close deals faster.
Building Your SOC 2 Type 2 Readiness Checklist
Trying to tackle a SOC 2 Type 2 audit without a solid plan is like navigating a storm without a compass. Getting "ready" isn't just a warm-up exercise; it's the bedrock of a successful audit. This is the stage where you turn abstract security principles into real-world, provable practices.
For smaller companies and startups, this phase can feel like a mountain to climb. The pain of manually gathering evidence is immense. You're probably familiar with the frantic search for screenshots, the sprawling spreadsheets trying to track controls, and the constant pull on your engineering team's valuable time. This chaos doesn't just slow you down—it opens up gaps that can lead to a dreaded audit exception. A structured checklist turns that scramble into a streamlined, methodical system.
Core Domains of Your Readiness Checklist
A good readiness checklist should be organized around the key control areas your auditor will be laser-focused on. While the specifics will hinge on which Trust Services Criteria you've selected, some domains are always in the spotlight. Let's break down the essentials and the kind of proof you'll need to start collecting.
1. Access Control
This is all about proving that only the right people can access your systems and data. It's the foundation of the Security (Common Criteria) TSC. Auditors will look for a formal, documented process for granting, changing, and—most critically—revoking access when someone leaves.
- Actionable Steps:
- Enforce Multi-Factor Authentication (MFA) across all critical systems.
- Implement Role-Based Access Control (RBAC) to ensure employees only have access to what they need.
- Create a formal process for onboarding and offboarding employees, including immediate access revocation upon departure.
- Schedule and conduct quarterly user access reviews for key systems.
2. Change Management
Auditors need to see you have a formal process for any changes made to your live environment. This ensures that updates don't accidentally create new security holes or break things for your customers. An environment where developers can push code whenever they feel like it is a huge red flag.
- Actionable Steps:
- Use a ticketing system like Jira to track all changes from request to deployment.
- Require peer review and manager approval for all code changes before they go live.
- Integrate automated testing and security scans into your CI/CD pipeline.
- Maintain a clear audit trail linking every deployment back to an approved change request.
The real headache for most engineering teams isn't putting these controls in place; it's proving they were followed consistently over the entire audit period. Manually digging up that evidence is a massive time-sink that pulls developers away from building your actual product.
Evidence Collection: From Chaos to Continuity
The sheer volume of evidence needed for a soc type 2 audit is what often trips up growing businesses. Picture this: your auditor asks for a sample of 15 approved change requests from the last nine months. For each one, you have to dig through old tickets, find the matching deployment logs, and take timestamped screenshots. That's hours of work for a single request.
This is where automation really shines. Instead of treating evidence gathering as a painful, one-off task, compliance automation platforms make it a continuous, background activity. They plug directly into your tech stack, automatically collecting proof as it happens and mapping it to the right SOC 2 controls. For teams already stretched thin, checking out the best compliance automation tools is a smart move towards a much smoother audit.
Essential SOC 2 Type 2 Evidence Examples
To give you a clearer picture, auditors will ask for concrete proof across several domains. It's not enough to say you have a policy; you need to show it's being followed.
The table below summarizes some of the most common types of evidence auditors will expect to see.
| Control Domain | Example Evidence Required |
|---|---|
| Risk Management | A formal risk assessment document with an identified risk register and corresponding mitigation plans, reviewed and approved annually by management. |
| Security Monitoring | Logs and alerts from your intrusion detection system (IDS) and security information and event management (SIEM) tools, along with documented procedures for responding to alerts. |
| Vendor Management | A list of critical third-party vendors, copies of their security certifications (like their own SOC 2 reports), and signed data processing agreements (DPAs). |
| Incident Response | An approved incident response plan, records of annual tabletop exercises or simulations, and detailed post-mortem reports from any security incidents that occurred. |
Think of this list as your starting point for building a comprehensive evidence library.
Putting together this checklist is your first major step from feeling anxious about compliance to feeling confident about your audit. It creates a clear, actionable roadmap, helping your team prepare systematically and avoid the last-minute fire drill that so many companies face.
How a SOC 2 Report Accelerates Your Sales Cycle

For a growing business, it’s easy to see compliance as just another cost centre—a box-ticking exercise that drains resources without bringing in revenue. But looking at a SOC 2 Type 2 report that way is a mistake. It misses the report's true power as a potent sales tool. This isn’t just about defense; it’s about going on the offensive to close bigger deals, faster.
When you're trying to sell to enterprise clients, security isn't just another bullet point on a feature list; it's the price of admission. They won't just take your word that their data is safe. They need hard proof. This usually comes in the form of massive security questionnaires—hundreds of questions that can bring a promising deal to a grinding halt for weeks, sometimes months.
The Master Key to Enterprise Deals
Think of your SOC 2 Type 2 report as a master key. It lets you skip the most grueling parts of the vendor security review. The moment your sales team can produce a clean, independent audit report, the entire conversation with a prospect changes. It becomes the definitive answer to the all-important question: "Why should we trust you with our data?"
Instead of tying up your engineers for hours or days to hunt down answers for a questionnaire, your sales rep simply hands over a single, authoritative document. This one move achieves several critical goals:
- Builds Instant Credibility: It shows a level of security maturity that immediately distinguishes you from less-prepared competitors.
- Reduces Sales Friction: It slashes the time spent in the security review phase, which is often where deals go to die.
- Answers Questions Proactively: The report covers the vast majority of a prospect’s security concerns before they even have to ask.
Turning Security from an Objection into an Advantage
Without a SOC 2 report, security is often a major sales objection your team has to painstakingly overcome. With one, it becomes a key part of your closing argument. It flips your security posture from a potential weakness into a proven strength, allowing your team to reframe the entire discussion.
The return on investment for a SOC 2 Type 2 report is crystal clear. It empowers your sales team to stop defending your security posture and start selling with it, turning a daunting hurdle into a genuine competitive edge.
This shift is especially powerful for startups trying to punch above their weight and land larger customers. With data breaches now costing US companies an average of $9.36 million, enterprise clients are more risk-averse than ever. They actively seek out partners who can provide undeniable proof of robust security controls. Your SOC 2 report is that proof.
The gains in efficiency aren't just a one-off, either. By using tools to automate compliance and manage security evidence, you can stay ready for these reviews at all times. Platforms designed for compliance management can dramatically reduce the manual effort needed to stay on track. You can explore compliance automation platform pricing options to see how this fits your budget and growth stage.
Ultimately, investing in a soc type 2 audit is a strategic move. It gives your revenue-generating teams the evidence they need to build trust, stand out from the crowd, and speed up the entire sales cycle—from the first call to the final signature.
Your SOC 2 Type 2 Questions, Answered
Let's be honest, navigating compliance can feel overwhelming, especially when your main focus is on building a great product. As a founder or team leader, you just need straight answers. Here are some of the most common questions we hear about the SOC 2 Type 2 process, answered simply and directly.
How Much Should I Budget for a SOC 2 Type 2 Audit?
The investment for a SOC 2 Type 2 audit really depends on the size of your company and the complexity of your systems. For most businesses, the all-in cost lands somewhere between $20,000 and $60,000+.
This range typically covers everything from initial readiness assessments and auditor fees to any specialized tooling you might need. One thing to keep in mind is that using a compliance automation platform can often bring that total cost down by cutting out hundreds of hours of manual work for your team.
How Long Does It Take to Get a SOC 2 Report?
Patience is key here. From the moment you decide to start until you have the final report in hand, you're usually looking at a 9 to 15-month journey.
This timeline is split into two distinct phases:
- The Readiness Phase (3-6 months): This is your prep time. You’ll be putting the necessary controls in place, documenting everything, and generally getting your house in order.
- The Observation Period (6-12 months): This is the main event. Your auditor will actively monitor and test your controls over this stretch to ensure they’re working as designed, day in and day out.
Getting a head start on your preparation is the single best way to keep your audit on track and avoid any last-minute hurdles that could slow down your sales conversations.
Is This Really Necessary for a Startup or Small Business?
In a word: yes. If you handle customer data and have your sights set on selling to mid-market or enterprise companies, a SOC 2 Type 2 report is non-negotiable.
It's no longer just a nice-to-have certification; it’s table stakes in the world of B2B SaaS. Many larger organizations won't even start a procurement conversation with a vendor that doesn't have one, making it an essential tool for unlocking growth.
For more deep dives into compliance topics and practical advice, we share a lot of insights on our company blog. Our goal is to help you turn security from a chore into a real competitive advantage.
Ready to transform security questionnaires from a sales blocker into a sales accelerator? Compli.st uses AI to complete them in minutes, not days. Our platform helps you build trust, shorten sales cycles, and free up your engineering team to focus on what they do best. Learn more about Compli.st.
Article created using Outrank