If you're a growing business, you've probably hit a wall in a sales conversation that sounds something like this: "Your product looks great, but how can we be sure you'll keep our data safe?" For many SMBs and startups, this is the moment the big enterprise deal stalls.
They need proof, not promises. This is where SOC 2 compliance stops being a technical chore and becomes your key to unlocking revenue.
Unlocking Enterprise Deals with SOC 2 Compliance

SOC 2 isn't just an IT framework; it’s a powerful sales tool. Developed by the American Institute of Certified Public Accountants (AICPA), it provides a formal report from an independent auditor that validates your security controls. In short, it’s the definitive answer to that tough question from your enterprise prospect, allowing you to bypass endless security questionnaires and move the deal forward.
Think of it as getting your company's data handling practices professionally certified. It's not a rigid, one-size-fits-all checklist. Instead, SOC 2 is a flexible framework that allows you to design and implement security controls that make sense for your business and the specific promises you make to your customers.
To help you get started, here's a quick rundown of the essential SOC 2 concepts.
SOC 2 at a Glance Key Concepts Explained
| Component | What It Means for Your Business |
|---|---|
| AICPA | The American Institute of Certified Public Accountants, the professional organisation that developed the SOC 2 framework. |
| Trust Services Criteria | The five core principles your controls are measured against: Security, Availability, Processing Integrity, Confidentiality, and Privacy. |
| Type I Report | An auditor's opinion on your controls at a single point in time. It shows you have a good design. |
| Type II Report | An auditor's opinion on your controls over a period of time (usually 3-12 months). It proves your controls are operating effectively. |
| Independent Auditor | A certified public accounting (CPA) firm that examines your controls and issues the final SOC 2 report. |
This table covers the basics, but the real power of SOC 2 lies in how it transforms your business operations and sales conversations.
Why SOC 2 Is a Business Accelerator
Achieving SOC 2 compliance directly tackles the biggest sales roadblock for growing companies: security objections. When a prospect asks for proof of your security, a SOC 2 report provides a trusted, third-party validated answer. This instantly moves the conversation from doubt to confidence, saving you from the dreaded security questionnaire death spiral.
This demand isn't just a hunch; it's a market reality. In the French cybersecurity market, an overwhelming 76% of businesses say their customers and partners now demand concrete proof of security. It's clear that SOC 2 is quickly becoming a standard expectation, not an exception.
By investing in SOC 2, you're not just ticking a box. You're building a foundation of trust that allows your organisation to:
- Enter new markets by satisfying the strict security demands of enterprise-level clients.
- Shorten sales cycles by addressing security concerns upfront, cutting down the back-and-forth during procurement.
- Gain a competitive edge over rivals who can't offer the same level of security assurance.
A SOC 2 report demonstrates that your organisation has established robust internal controls to secure the services you provide. It is the gold standard for validating your commitment to protecting customer data.
More Than a Report A Framework for Trust
Ultimately, SOC 2 compliance changes the entire dynamic. It stops being a costly chore and becomes a strategic investment in your company's growth and reputation. It's the key that unlocks bigger deals, builds lasting customer confidence, and proves your security is as solid as your product.
Understanding the journey to SOC 2 certification is the first step toward using this powerful asset to accelerate your business.
Understanding The Five Trust Services Criteria
At the heart of any SOC 2 audit are the Trust Services Criteria (TSCs). These are the principles the AICPA created to measure how well you're protecting customer data. Don't think of them as a rigid checklist, but as a menu of security promises. Your job is to select the criteria that match the commitments you've made to customers and then prove you’re living up to them.
The framework is built on five core principles. They might sound technical, but each one maps directly to a real-world business promise. Understanding them is the first step toward a meaningful—and cost-effective—audit.
Security: The Mandatory Foundation
The Security criterion is the one you can't skip. Often called the Common Criteria, it’s the non-negotiable foundation for every single SOC 2 report. No matter what your business does, this has to be in your audit. It all boils down to one fundamental question: is your system protected against unauthorised access, both digitally and physically?
This criterion looks at essential security practices every technology company should be doing anyway. It's about having the right controls for your infrastructure, your software, the people you employ, and the procedures you follow to keep everything secure.
For example, controls under the Security criterion often include things like:
- Access Controls: Ensuring only the right people can get into sensitive systems, using tools like multi-factor authentication (MFA) and role-based permissions.
- Firewall Configuration: Setting up and maintaining network firewalls to block malicious traffic and shield your internal network.
- Intrusion Detection: Using systems that monitor network activity for anything suspicious and can alert you to a potential breach.
- Employee Vetting: Running background checks and providing security training for new hires who will have access to customer data.
The Security criterion is foundational because it tackles the universal need to protect information. Without these baseline controls, any promises you make about availability or confidentiality just wouldn't hold water.
Choosing Your Additional Criteria
Once you have Security covered, you can choose to add any of the other four TSCs to your audit. This is a crucial strategic decision that should be driven entirely by your customer contracts and Service Level Agreements (SLAs). Adding criteria you don't need is a classic way to waste time and money, so choose carefully.
Just ask yourself: what promises are we making? Do we guarantee a certain level of uptime? Do we handle sensitive financial data? The answers will point you to the right criteria.
Availability: Is Your Service Always On?
The Availability criterion is for any business that promises a high level of uptime. If your customers' operations depend on your platform being accessible and running smoothly, then this TSC is essential. It's how you prove you have the right controls in place to meet your performance commitments.
A SaaS platform with a 99.9% uptime SLA, for instance, would absolutely need to include Availability. The controls here would involve things like performance monitoring, solid disaster recovery plans, and incident response procedures designed to get the service back online fast.
Processing Integrity: Is Your Data Accurate?
Processing Integrity is all about the accuracy, completeness, and timeliness of how your system handles data. This one is crucial for services where every transaction has to be perfect, like e-commerce checkouts or financial processing systems. It proves your system does what it's supposed to do, without errors or manipulation.
Think about a fintech app that processes payments—it has to ensure every single transaction is handled correctly. This means having controls like data validation checks and detailed processing logs to maintain a clear and trustworthy audit trail.
Confidentiality: Is Your Data Kept Secret?
The Confidentiality criterion is focused on protecting information that is meant to be restricted to a specific group of people. This is a step beyond general security; it’s about specific contractual or legal promises you’ve made to keep certain data under lock and key.
A legal tech platform handling sensitive case files is a perfect example. To meet this criterion, they would need controls like robust data encryption (both for data in transit and at rest) and extremely strict data access policies to prevent any unauthorised disclosure.
Privacy: Is Personal Information Handled Correctly?
Finally, the Privacy criterion covers how you collect, use, store, and eventually dispose of personal information. It aligns very closely with data protection regulations like GDPR. This is non-negotiable for any business that handles personally identifiable information (PII) and makes specific privacy commitments to its users.
A health-tech app that collects patient data, for example, must follow strict privacy controls. This includes giving users clear privacy notices and always honouring their choices about how their data is used. Choosing the right set of criteria is what turns a SOC 2 audit from a simple compliance exercise into a powerful business strategy.
Choosing Your Path: SOC 2 Type 1 vs. Type 2
One of the first big decisions on your SOC 2 journey is picking the right report: Type 1 or Type 2. It’s a choice that directly impacts your timeline, budget, and even your sales cycle. For a startup, this feels like a confusing fork in the road, but it’s straightforward once you understand what each report is designed to do.
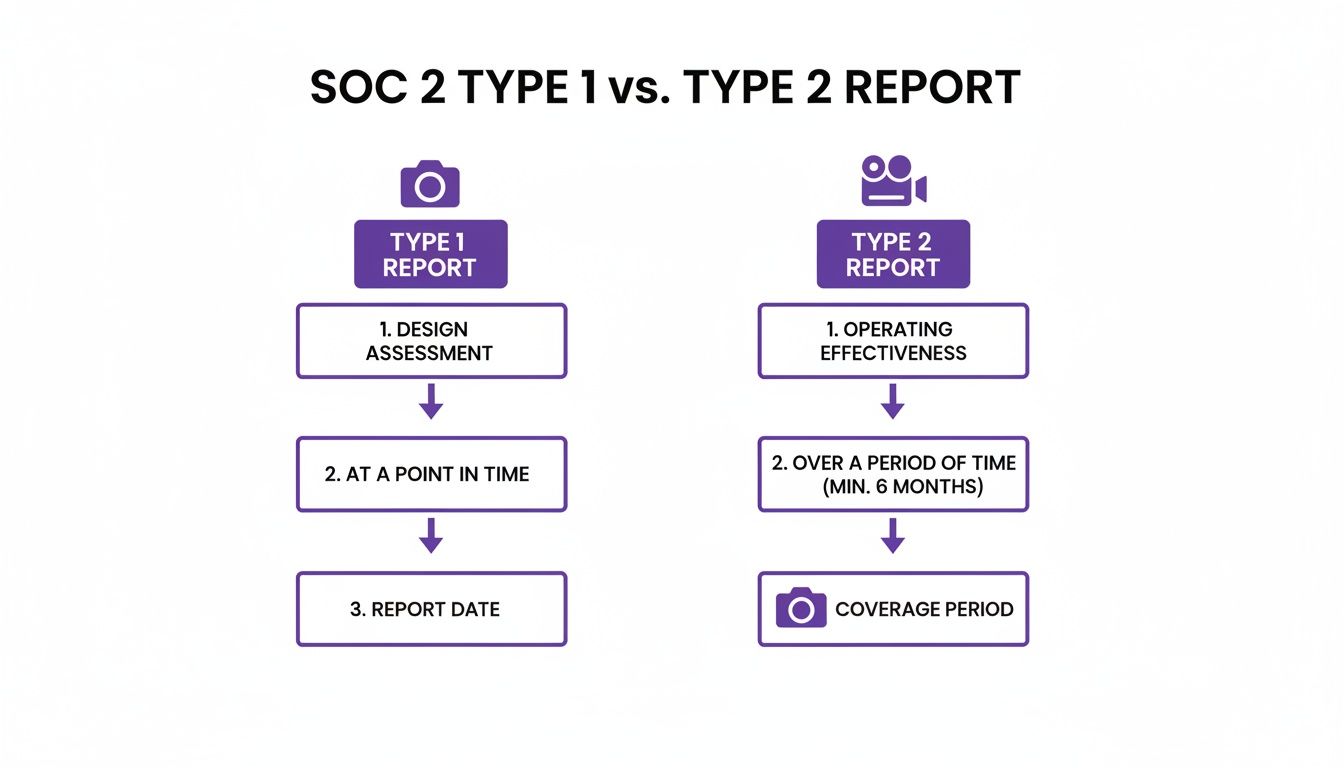
Think of it this way: a SOC 2 Type 1 report is a blueprint. An auditor examines your security controls at a single moment and confirms that, on paper, you’ve designed a solid system. It answers the question, "Have you documented the right security measures?"
A SOC 2 Type 2 report, on the other hand, is the stress test. It goes much further by testing whether those controls have actually been working as intended over a longer period, usually six to twelve months. This report answers a far more compelling question: "Does your security system hold up in the real world, day after day?"
The Strategic Value of a SOC 2 Type 1 Report
For many growing companies, starting with a Type 1 report is a brilliant strategic move. The biggest advantage? Speed. Since the audit only looks at the design of your controls on a specific date, you can achieve it much faster than a Type 2.
This speed makes it a powerful tool for getting sales deals unstuck. When a prospect’s security team demands your SOC 2, a Type 1 report shows you’re serious and have a well-designed security program in place. It’s often the proof they need to move the deal forward while you work towards a Type 2.
The Gold Standard: The SOC 2 Type 2 Report
While a Type 1 report gets you in the door, a SOC 2 Type 2 report is what seals the deal with larger, more mature customers. It’s considered the gold standard in security assurance because it offers concrete proof that your controls are consistently effective over time.
For enterprise clients with strict vendor risk management programs, a Type 2 report isn’t just nice to have—it’s often a deal-breaker.
A SOC 2 Type 2 isn't just a compliance milestone; it's a testament to your organisation's operational excellence and long-term commitment to protecting customer data. It signals a mature and reliable security posture.
Achieving a Type 2 shows that security is baked into your company’s culture, not just a one-off project. It builds the deep, lasting trust required to win and retain your most valuable customers. For a deeper dive, check out our detailed guide on the SOC 2 Type 2 audit process.
SOC 2 Type 1 vs Type 2: A Strategic Comparison
Deciding between a Type 1 and Type 2 report comes down to your immediate business goals and customer expectations. This table breaks down the key differences to help you make the right call.
| Attribute | SOC 2 Type 1 Report | SOC 2 Type 2 Report |
|---|---|---|
| Purpose | Assesses the design of controls at a single point in time. | Tests the operating effectiveness of controls over a period (6-12 months). |
| Timeline | Faster (typically 1-3 months for readiness and audit). | Longer (requires a 6-12 month observation period plus audit time). |
| Effort | Less intensive; focuses on documentation and implementation. | More intensive; requires evidence collection over the entire audit period. |
| Cost | Lower, due to the shorter audit scope and timeline. | Higher, reflecting the extended duration and depth of testing. |
| Best For | Unblocking sales quickly, meeting initial customer requests, and building a foundation. | Meeting enterprise requirements, demonstrating mature security, and building long-term trust. |
Ultimately, many companies start with a Type 1 to secure early wins and then progress to a Type 2 as their business scales and their customers' demands grow. It’s not an either/or forever choice, but a strategic progression.
Your Roadmap to a Successful SOC 2 Audit
Stepping into your first SOC 2 audit can feel overwhelming. It's a major undertaking, but with a clear roadmap, you can turn a daunting process into a manageable, step-by-step plan. A structured approach is everything—it helps you sidestep expensive delays and avoid last-minute panic.
The entire process is won or lost in the preparation. You cannot afford to wait for an auditor to show up and tell you what's broken. That's a surefire way to fail. A clean audit is the direct result of careful, methodical planning that starts months before the official audit window even opens.
Phase 1: Scoping Your Audit and Performing a Gap Analysis
First, you need to define your scope. This means clearly identifying which systems, data, people, and processes are being audited. A classic startup mistake is casting the net too wide, pulling in systems that have nothing to do with your service delivery. This just adds unnecessary complexity and cost. Be surgical and focus only on what's essential.
With your scope locked in, it's time for a gap analysis. Think of this as a pre-audit health check. You'll compare your current security controls against the specific SOC 2 Trust Services Criteria you're aiming for. This reveals where you're solid and, more importantly, where you have gaps that need fixing before the auditor sees them.
A good gap analysis becomes your project plan, giving you a prioritised to-do list for getting audit-ready.
Phase 2: Implementing Controls and Gathering Evidence
Now that you know where the gaps are, the real work begins. This is the remediation phase, where you’ll roll out new controls, update policies, and configure systems to meet SOC 2 standards. This might mean enforcing multi-factor authentication everywhere or formalising your incident response plan.
As you implement these controls, you must start gathering proof that they're working. This is where most teams get bogged down. Manually grabbing screenshots, pulling logs, and documenting procedures is a soul-crushing, time-consuming task that pulls your engineers away from building your product.
The sheer grind of manual evidence collection is one of the biggest bottlenecks in any SOC 2 project. This is where modern automation tools really shine; they plug directly into your tech stack and continuously gather the proof you need, without anyone having to lift a finger.
This is especially true when you consider the two main types of SOC 2 reports.
The image really highlights why a Type 2 report, which looks at your controls over a long period, benefits so much from an automated, continuous approach to evidence gathering.
Phase 3: Navigating the Audit and Beyond
After months of hard work, you’re ready for the audit. Your chosen CPA firm will conduct their fieldwork, reviewing the evidence you’ve collected and testing your controls. If you've prepared correctly, this should feel like a smooth validation of your efforts, not a frantic, stressful scramble.
The need for this kind of rigorous proof is only growing. French companies, for instance, are increasingly seeing audits as a regular activity, not a one-off event. Market trends show that 92% plan to conduct at least two audits in 2025, with a surprising 58% aiming for four or more. This reflects a bigger shift where frameworks like SOC 2 are becoming critical for navigating regional regulations. If you want to dig deeper, you can explore the full research on compliance statistics.
Getting your SOC 2 report is a huge win—it’s a powerful asset for your sales and security teams. But the journey isn't over. Compliance is a continuous effort. You have to keep operating and monitoring those controls to maintain your security posture and be ready for next year's audit.
By following this roadmap, you can demystify the process and turn SOC 2 compliance into a genuine strategic advantage that builds customer trust and helps you close bigger deals, faster.
How Automation Accelerates SOC 2 Compliance
For any growing startup, the journey to SOC 2 compliance often feels like a painful, uphill battle fought in spreadsheets. The reality of manual compliance is a gruelling slog of taking screenshots, chasing down engineers for evidence, and trying to map hundreds of controls across endless Excel rows. This process doesn't just kill morale; it pulls your best technical minds away from what they should be doing—building your product.
This manual grind is where the hidden cost of compliance really bites. Every hour an engineer spends digging through logs for an auditor is an hour they aren't shipping features that generate revenue. The whole thing becomes a resource-heavy, error-prone ordeal. This is precisely the pain point that modern compliance automation was built to solve.

Continuous Control Monitoring and Evidence Collection
Picture a system that acts like a 24/7 security analyst, constantly scanning your cloud environment to ensure your controls are working. That’s the power of automated platforms designed for SOC 2. These tools integrate directly with your core tech stack—like AWS, Google Cloud, GitHub, and your HR systems.
Instead of manual spot-checks before an audit, the platform provides continuous control monitoring. It automatically confirms your security settings are configured correctly, that multi-factor authentication is enforced everywhere, and that access permissions haven't drifted out of line.
When the audit rolls around, the evidence is already there, perfectly organised and ready to go.
- Automated Evidence Gathering: The platform pulls logs, configurations, and policy documents straight from the source. No more manual screenshots.
- Real-Time Alerts: If a control fails—say, a security group is misconfigured in AWS—the system flags it immediately, letting you fix things long before an auditor sees them.
- Reduced Engineering Load: By taking this work off their plate, you free up your engineers to focus on your product, not on compliance busywork.
Automation transforms SOC 2 compliance from a disruptive, point-in-time event into a quiet, continuous process. It embeds security and compliance into your daily operations, making you audit-ready at all times.
From Blank Pages to Audit-Ready Policies
Beyond the technical checks, one of the most time-consuming parts of any SOC 2 project is writing the dozens of required security policies. For a startup without a dedicated compliance team, starting from scratch is overwhelming. This is another area where automation provides a huge head start.
Compliance platforms typically come with libraries of pre-built, auditor-vetted policy templates. These aren't just generic documents; they’re specifically designed to meet SOC 2 criteria. This feature alone can save a team hundreds of hours of research, writing, and legal review. You can quickly adopt and tailor templates for key areas like:
- Information Security
- Acceptable Use
- Incident Response
- Change Management
These platforms streamline the entire journey. When you combine automated monitoring, continuous evidence collection, and ready-made templates, a resource-draining compliance project becomes a genuine business advantage. It helps you get your SOC 2 report faster, prove your security to big clients, and ultimately, close bigger deals without derailing your product roadmap. Exploring the landscape of these tools is a crucial next step; you can get a better sense of the market by reviewing a breakdown of the 5 best Vanta alternatives to see how different platforms tackle these challenges.
Your SOC 2 Compliance Questions Answered
When you're first diving into SOC 2, a lot of practical questions come up. For startups and growing businesses, understanding the real-world costs, timelines, and effort involved is crucial for good planning. Here are some straightforward answers to the questions we hear most often.
Our goal here is to cut through the jargon and give you the practical insights you need to make SOC 2 compliance a genuine asset for your business, not just another box to tick.
How Much Does SOC 2 Compliance Cost?
The final cost depends on your company's size, system complexity, and which Trust Services Criteria you include. Your main costs will be the auditor's fees and any compliance automation software you use.
While the initial investment can look steep, consider the ROI. A compliance automation platform drastically cuts down the hours your own engineering team would otherwise spend manually gathering evidence—often the biggest hidden cost. It's better to see SOC 2 not as an expense, but as an investment in a powerful sales tool that unlocks access to larger, more valuable enterprise customers.
How Long Does It Take to Get a SOC 2 Report?
The timeline depends almost entirely on your current security posture. For a SOC 2 Type 1 report, which just looks at the design of your controls, you can often get it done in 3-6 months if you have solid security practices in place.
A SOC 2 Type 2 report is a bigger commitment. It requires an observation period, typically 6-12 months, to prove your controls work effectively over time. This is where automation is a game-changer. A platform with pre-built controls and automated evidence gathering can shrink the readiness phase from months down to just a few weeks, getting you in front of an auditor much sooner.
Automation transforms SOC 2 readiness from a long, disruptive project into a streamlined, efficient process. It helps you get to the audit stage faster, so you can start leveraging your report in sales conversations sooner.
Do We Need a Penetration Test for SOC 2?
Great question. While a penetration test isn't explicitly mandatory in the official SOC 2 guide, it has become a standard expectation. Auditors now commonly look for a recent pen test report as powerful evidence that you're meeting key requirements within the Security criterion.
Think of it this way: it’s the best way to prove your defenses can hold up against a real-world attack. Being proactive about getting a penetration test not only strengthens your security but also makes the audit itself go much more smoothly. It shows you're taking risk management seriously.
Can We Achieve SOC 2 Compliance Without an Automation Tool?
Technically, yes, it's possible. But for a fast-moving startup, it’s a painfully inefficient and resource-draining approach. Going manual means living in spreadsheets, taking endless screenshots, and constantly pulling your engineers away from building your product to chase down evidence.
This old-school method isn't just tedious; it's also prone to human error and simply doesn't scale. A compliance automation platform centralizes all your control management and evidence collection. It turns a frustrating, manual chore into a sustainable, strategic advantage that helps you build trust and win more business.
Ready to transform your compliance journey from a manual burden into a sales accelerator? Compli.st uses AI to automate evidence collection for SOC 2 and other frameworks, and completes security questionnaires in minutes. Discover how you can get audit-ready faster and close deals with confidence.