For any growing startup or SMB, a data leak is more than just an IT hiccup—it's a potential deal-breaker that can kill your sales pipeline and destroy customer trust. When you implement robust data leakage prevention solutions, you’re not just spending on security. You're making a strategic investment that smashes through the security hurdles that stall sales cycles and helps you close bigger deals, faster.
Why Data Leakage Prevention Is a Business Growth Engine

In the world of startups and SMBs, every single sales conversation counts. But imagine this painful scenario: a promising enterprise deal suddenly grinds to a halt over one simple question on a security questionnaire: "How do you prevent data leakage?" If you don't have a solid, demonstrable answer, you're not just delaying the sale; you're planting a seed of doubt that could cost you the entire contract.
Think of your company's sensitive data as its crown jewels. A Data Leakage Prevention (DLP) solution is your intelligent, 24/7 security system guarding those jewels from being accidentally exposed or deliberately stolen. More importantly, it gives you concrete proof of your security posture to satisfy those discerning enterprise clients and pass their vendor reviews.
Turning Security Into a Competitive Advantage
Putting a DLP system in place is about much more than just defence—it’s about enabling growth. When you can clearly demonstrate strong data governance, you build the kind of trust that helps you close bigger contracts, and faster. It sends a clear signal that you are a mature, reliable partner, not a risky startup.
This proactive security stance brings several key benefits to the table:
- Accelerated Sales Cycles: Breeze through security questionnaires with confidence, turning what was once a bottleneck into a smooth, automated process.
- Increased Client Trust: Prove your commitment to data protection to win bigger deals with enterprise clients who have much higher security standards.
- Simplified Compliance: A DLP system provides the auditable evidence you need to achieve and maintain frameworks like ISO 27001, SOC 2, NIS 2, and DORA.
A strong data protection strategy is no longer a "nice-to-have." For ambitious SMBs, it’s a foundational element for building trust, satisfying enterprise-level procurement, and unlocking new revenue streams.
Meeting Modern Compliance Demands
As regulations get stricter, simply saying you’re secure is not enough—you have to prove it. For instance, achieving and maintaining compliance frameworks is a critical step for many B2B companies. A DLP solution directly supports this goal. Take a look at our guide on the path to SOC 2 certification to see just how central data protection controls are.
The market statistics tell the same story. Europe holds a significant share of the global Data Leak Prevention Software Market, with France, Germany, and the UK leading the way in adoption. This trend is largely driven by the strict enforcement of GDPR and other sector-specific regulations. You can find more detail on this in the Data Leak Prevention (DLP) Software Market report. This focus on data sovereignty proves that building DLP into your digital strategy is a recognised path to tangible economic rewards.
How Does a DLP Solution Actually Work?
To really get a feel for what a Data Leakage Prevention solution does, you have to look under the hood. Don't think of it as a single, blunt instrument. Instead, picture it as a highly specialized security team, with each member trained for a specific role in protecting your company's crown jewels—your customer data, financial records, and intellectual property.
This team operates across four critical areas, making sure your data is secure no matter where it is, how it’s moving, or who is using it. This layered approach is what elevates a simple tool into a robust system that truly protects the business.
Discovering Where Your Sensitive Data Lives
You can't protect what you don't know you have. That’s why the first and most fundamental job of any DLP solution is Data Discovery and Classification. It’s like sending in an expert archivist to systematically scan every corner of your digital estate—from cloud storage and databases to individual employee laptops.
The goal is simple: find, identify, and tag sensitive information. These systems are trained to spot patterns that flag high-value data, such as:
- Personally Identifiable Information (PII) like national insurance numbers or passport details, which are critical for GDPR and SOC 2.
- Financial Data including client credit card numbers or confidential quarterly reports, essential for DORA compliance.
- Intellectual Property (IP) such as proprietary source code, top-secret design documents, or strategic business plans—the very lifeblood of your startup.
Once found, the data is classified based on its sensitivity. This crucial step ensures you apply the right level of protection to the right information, a core requirement of ISO 27001.
Protecting Data As It Moves
Data rarely sits still; it’s constantly being sent, shared, and accessed. This is where Data in Motion protection kicks in, acting as a vigilant gatekeeper monitoring all the exit points of your network.
Imagine the pain of a sales rep accidentally emailing your entire client list to their personal account for some "weekend work." A DLP solution spots this in real-time. It understands the context—a large volume of sensitive PII leaving the network for an unauthorized destination—and can automatically block the email and notify a manager, preventing a major compliance incident.
This isn’t just about stopping malicious acts. More often, it’s about preventing costly accidents. A good DLP solution is a critical safety net, catching human error before it escalates into a full-blown data breach that could kill a funding round or a major deal.
Securing Data Where It Is Stored
Vast amounts of your most valuable information are tucked away in various locations. Data at Rest protection focuses on securing this stored information, whether it’s in a shared cloud drive like Google Drive, a structured database, or a folder on a local server.
This component continuously scans these storage locations for weaknesses. It checks that sensitive files are properly encrypted, that access permissions are correctly configured, and that no unauthorized copies are being made. If it finds a misconfiguration—like a folder of customer contracts accidentally made public—the DLP system can automatically fix the permissions or quarantine the files, demonstrating proactive risk management to auditors.
For a deeper dive into the techniques for preventing data loss from physical devices, this guide to secure destruction of data is an excellent resource.
Monitoring Data During Active Use
Finally, data is often most vulnerable when it's being actively handled on an employee's device. Data in Use protection tackles this by monitoring actions on endpoints like laptops and desktops. It’s the digital equivalent of having a security officer looking over an employee's shoulder.
For instance, if someone tries to copy sensitive client details from a protected document and paste them into an unsecured app like a public chat tool, the DLP agent on their machine can block the action instantly. It can also prevent data from being moved to unauthorized USB drives or printed without justification, ensuring your data stays within your control even as your team gets their work done.
Connecting DLP Features to Business Outcomes
It's one thing to understand the technical functions of DLP, but it's another to see how they translate into real-world business value. The following table connects the dots between each core component and its direct impact on your SMB's security, compliance, and bottom line.
| DLP Component | Technical Function | Business Impact for SMBs & Startups |
|---|---|---|
| Data Discovery & Classification | Scans and tags sensitive data across all systems. | Provides a clear inventory of critical data assets, enabling risk-prioritized security policies and satisfying core requirements for ISO 27001 and SOC 2. |
| Data in Motion (Network) | Monitors and controls data leaving the network perimeter. | Prevents accidental emails and unauthorized file transfers, reducing the risk of a breach that could trigger massive GDPR fines and destroy client trust. |
| Data at Rest (Storage) | Secures data stored in databases, cloud services, and file servers. | Protects against unauthorized access to stored data and ensures encryption and access controls are properly enforced, a key control for nearly all compliance frameworks. |
| Data in Use (Endpoint) | Controls actions like copy/paste, printing, and USB transfers. | Stops insider threats and accidental leaks at the source, securing data even when employees are working remotely and helping answer tough security questionnaire questions. |
Ultimately, a well-implemented DLP solution moves beyond just being a set of technical controls. It becomes a strategic asset that directly supports business objectives by safeguarding intellectual property, maintaining customer trust, and avoiding the steep costs associated with a data breach.
Choosing the Right DLP Architecture for Your Company
Picking a data leakage prevention solution isn't about finding a single "best" tool. It’s about matching the architecture to your specific business needs. A mismatch is more than just a bad investment; it creates genuine security gaps. For SMBs and startups, getting this right from the start is critical to protecting your data without bogging down your agile team in needless complexity.
Think of your company's data ecosystem as a physical office campus. You wouldn't use the same security measures for every part of it, would you? You'd have guards patrolling the perimeter, others checking IDs at building entrances, and maybe a high-tech vault for your most valuable assets. DLP architectures work in a similar, layered way.
The first step is to get a clear picture of where your most sensitive data lives and how your team actually works with it. A company with a fully remote team using cloud apps all day has a completely different risk profile than one operating from a central office with on-premise servers. Your choice has to reflect your operational reality.
Network DLP: The Perimeter Guard
Network DLP solutions are like the main security gate for your entire digital campus. They are installed where your internal network meets the outside world—the egress points—and they inspect all the traffic heading out.
This architecture is fantastic at catching data in motion. It watches over emails, web uploads, and file transfers, making it highly effective at stopping large-scale data theft, like someone trying to upload your entire customer database to a personal cloud drive.
- Best for: Organizations with a well-defined network perimeter and a lot of on-premise infrastructure.
- Limitation: Its biggest blind spot is what happens when people leave the network. It offers little to no protection for remote workers or data on their mobile devices, a major gap for modern startups.
Endpoint DLP: The Lock on Every Door
If Network DLP is the main gate, then Endpoint DLP is the high-security lock on every single office door. This approach works by installing a software agent directly onto employee devices like laptops and desktops.
This gives you incredibly granular control over data in use. It can monitor and block actions like copying sensitive files to a USB stick, pasting confidential text into a personal email, or even taking a screenshot of a protected document. Because the agent lives on the device, the protection travels with the employee, which is perfect for today’s remote and hybrid teams.
Endpoint DLP is often the cornerstone of a modern security strategy because it directly addresses the reality of a distributed workforce. It ensures your data remains protected no matter where your team members are working from.
The decision tree below can help you visualize which type of protection is needed based on your data's state—whether it's in motion, at rest, or in use.
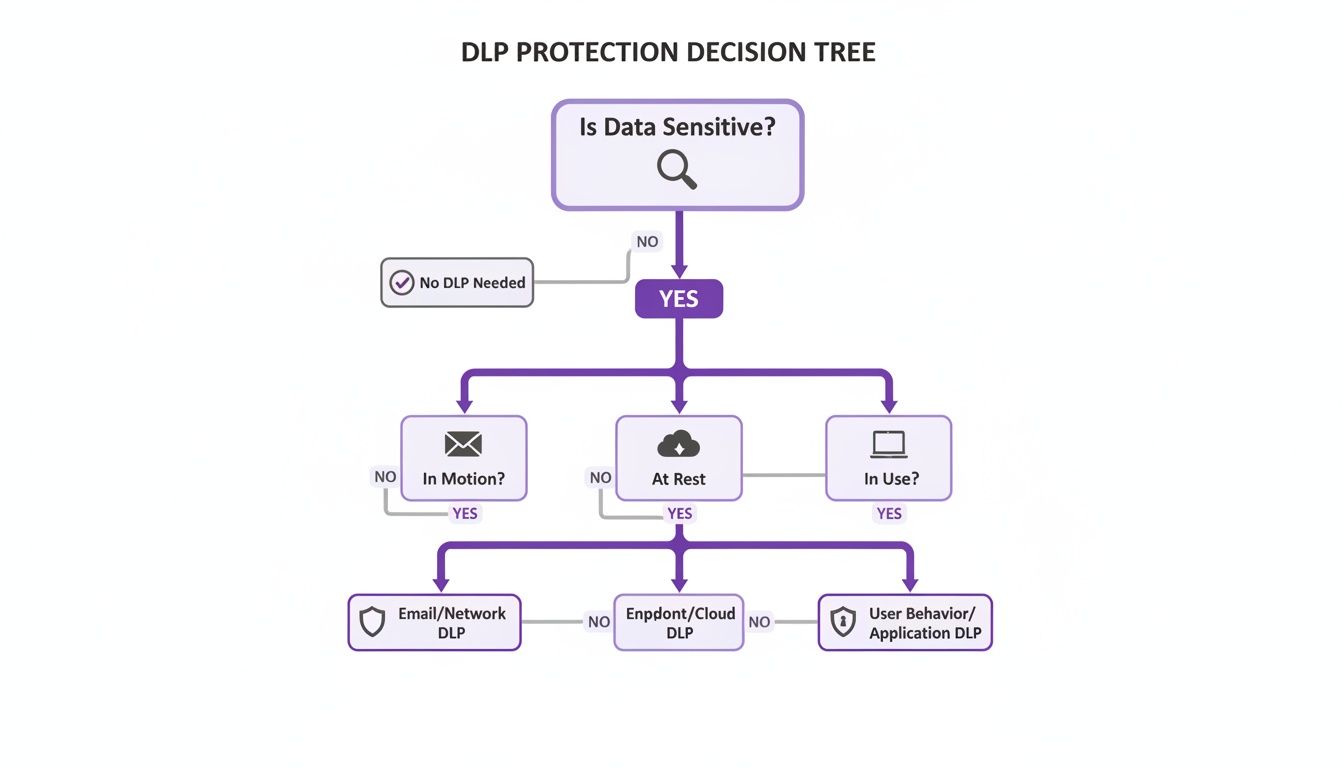
As you can see, a complete strategy often means protecting data in all its states, which is why so many businesses end up with a hybrid approach.
Cloud DLP: The Off-Site Vault Security
With so many critical operations now living in the cloud, Cloud DLP has become an absolute necessity for modern businesses. This architecture is built specifically to protect data at rest within services like Google Workspace, Microsoft 365, and AWS.
Cloud DLP solutions plug directly into these platforms using APIs. From there, they can scan for sensitive information, enforce your sharing policies, and spot dangerous misconfigurations—like an S3 bucket accidentally left open to the public. It's specialized security for your off-site assets, making sure your cloud footprint follows your data governance rules. Choosing the right architecture is a foundational element of your security program, and for those aligning with formal frameworks, you can learn more about building a solid foundation with risk management for ISO 27005.
For most modern SMBs and startups, a single architecture just won't cut it. The reality is that a hybrid approach, usually combining the strengths of Endpoint and Cloud DLP, offers the most robust protection. This ensures your data is secure both on employee devices and within the cloud apps they rely on every day—a true reflection of how modern work gets done.
Your Practical DLP Implementation Checklist
Rolling out a data leakage prevention solution can feel like a huge project, especially for a lean startup. But with a solid plan, it’s much more manageable than it seems. This actionable checklist is designed to help SMBs and startups get their DLP program off the ground smoothly, protecting critical data without grinding business to a halt.
Think of this as your roadmap. It takes the guesswork out of the process, helping you build a DLP strategy that not only works from day one but also gets smarter over time.
Step 1: Identify and Classify Your Critical Data
The first rule of data protection is simple: you can’t protect what you don’t know you have. Before you even touch a policy setting, you need to get a handle on your data. This discovery and classification process is the foundation for everything that follows.
Start by figuring out what sensitive information your company actually manages. This usually falls into a few key categories:
- Customer Information: This is the obvious one—Personally Identifiable Information (PII) like names, addresses, and contact details. A leak here can trigger GDPR fines.
- Financial Data: Think credit card numbers, internal financial reports, and confidential client billing records. This is critical for SOC 2 and DORA.
- Intellectual Property (IP): This is the company's secret sauce—proprietary source code, product roadmaps, and sensitive business strategies. Protecting this is vital for survival.
Once you know what you're looking for, you need to find out where it is. Scan your cloud storage, databases, email servers, and employee laptops to build a complete map of your data. Then, tag that data based on its sensitivity level (e.g., Public, Internal, Confidential, Restricted). This step ensures you’re aiming your strongest defenses at your most valuable assets.
Step 2: Begin in Monitor-Only Mode
It's tempting to flip the switch on a new DLP solution and set everything to "block" right away. This is almost always a mistake. It causes chaos, breaks legitimate workflows, and unleashes a storm of false positive alerts. The smarter, more actionable approach is to start in a passive, monitor-only mode.
Think of this as a reconnaissance mission. For the first few weeks, maybe even a month, your DLP tool will just watch and learn. It will log how data moves around your organization without actually stopping anything.
This observation period gives you a real-world picture of your data flows. You'll see how teams actually collaborate, what tools they use, and where your planned policies might cause friction. This ground truth is gold when it comes to writing rules that protect the business without killing productivity.
This approach lets you establish a baseline without frustrating your team. It gives you the evidence you need to build practical, effective policies in the next step.
Step 3: Methodically Refine Policies
Armed with insights from your monitoring phase, you can start building and fine-tuning your DLP policies. The key here is to be precise and methodical. The goal is to catch real risks, not create alert fatigue with endless false alarms.
Start small with your most critical, easy-to-define data. For instance, create a simple policy that triggers an alert when an outbound email contains more than 50 credit card numbers. See how it works in the wild.
Once that rule is performing well, you can gradually expand its scope or introduce more nuanced policies. Test every new rule, look at the alerts it generates, and tweak it based on feedback. This iterative process makes sure your policies are accurate and reflect how your business actually works, so security becomes an enabler, not a roadblock.
Step 4: Establish a Clear Incident Response Protocol
A DLP alert is useless if no one knows what to do with it. Without a clear plan, critical warnings get lost in the noise, and the whole point of having the solution is defeated. You need a straightforward incident response protocol.
This plan should spell out:
- Who gets the alert? (e.g., the user's manager, the IT security lead).
- What are the first steps? How do you verify if it's a real risk or a false positive?
- What's the escalation path? Who gets involved for low, medium, and high-severity incidents?
- What are the remediation actions? This could be anything from coaching the user to revoking access or even reporting a breach under NIS 2 or GDPR timelines.
Write this plan down and make sure everyone involved knows their role. This creates a consistent, timely, and effective response every single time.
Step 5: Train Your Team on Secure Data Handling
At the end of the day, technology is only part of the solution. Your employees are your first line of defense, which makes ongoing training non-negotiable for a successful DLP program.
Keep the training practical and based on real-world situations. Show your team why certain data is sensitive and give them clear, simple guidelines on how to handle it. It's also crucial to explain the purpose of the DLP tool—position it as a safety net designed to prevent accidents, not as a "big brother" tool watching their every move.
When people understand their role in protecting company data, they become partners in your security efforts. That cultural shift is what turns a DLP implementation from a technical control into a genuine organizational strength.
Using DLP to Streamline Your Compliance Efforts

For a growing SMB, tackling compliance frameworks like ISO 27001, SOC 2, NIS 2, or DORA can feel like a mountain to climb. The pain of manual evidence collection, endless spreadsheets, and audit preparation can grind your team to a halt. In this context, a data leakage prevention solution isn't just another security tool—it’s a powerful ally that automates and simplifies compliance.
Think of it this way: instead of scrambling to manually collect evidence for an audit, your DLP system is already doing the work. It provides a real-time, automated log of how you’re protecting sensitive information. This gives you the concrete proof auditors and enterprise clients demand, turning compliance from a reactive headache into a proactive strength.
Mapping DLP Features to Specific Compliance Controls
The real magic of a good DLP solution is how neatly its features map directly to specific regulatory controls. This creates a clear, auditable trail, demonstrating your commitment to data protection without your team having to spend weeks digging through logs and records.
It’s like having an automated assistant constantly gathering the exact evidence you need to pass an audit with flying colours. This direct link between your tools and the rules simplifies everything.
Here’s a practical look at how key DLP features line up with common compliance demands:
- Asset Management and Data Classification: Most frameworks (especially ISO 27001) require you to maintain an inventory of your data assets. A DLP’s discovery and classification capabilities handle this automatically. By finding and tagging sensitive data, you can prove to auditors that you know precisely where your critical information lives.
- Access Control Policies: Endpoint DLP is all about enforcing rules on who can access, copy, or move certain data. Every action is logged, providing verifiable proof that you're upholding the "principle of least privilege"—a non-negotiable for frameworks like SOC 2 certification.
- Secure Data Transfer: Controls governing data transfer are central to nearly every regulation. Network DLP monitors all data leaving your network, giving you undeniable evidence that you have robust technical measures in place to stop unauthorized data exfiltration. You can learn more about the specific controls in our ISO 27001 Annex A guide.
Automating Responses and Building Trust
Let's talk about a major pain point for SMBs: the dreaded security questionnaire from a potential enterprise client. A well-configured DLP system is a game-changer here. The detailed logs and reports it produces become your go-to resource for answering those tough technical questions with precision and proof.
Instead of scrambling for answers, your DLP system provides a single source of truth about your data protection practices. This allows you to build a powerful, evidence-backed Trust Center that answers client questions before they're even asked, accelerating deals and building confidence.
This approach flips the script, turning a DLP solution from a cost center into a genuine revenue enabler. It provides the assurance that large clients demand, which helps shorten sales cycles and positions your company as a secure, trustworthy partner.
Demonstrating ROI Beyond Security
The financial case for linking DLP with compliance is clear. A study from the French data protection authority, CNIL, found that Data Protection Officers who use DLP tools give their companies a serious advantage in tenders and help them avoid massive fines. This is especially true as breaches continue to rise across the health, finance, and IT sectors.
Beyond specific industry standards, sticking to broad data protection laws is essential. For instance, following strong GDPR compliance guidelines is not optional, and a DLP solution is one of the most effective ways to enforce and prove you're doing so. By providing tangible evidence of control, DLP helps you satisfy auditors, close bigger deals, and protect your business from both financial hits and reputational damage.
How to Measure DLP Success and Avoid Common Pitfalls
Getting a data leakage prevention solution up and running is a significant project, but the real work starts the moment you flip the switch. How can you be sure your investment is paying off? True success isn’t just about the number of incidents you block; it’s about making your security program smarter, more efficient, and directly supportive of your business objectives.
To measure success, you have to look past the raw alert numbers and focus on Key Performance Indicators (KPIs) that actually mean something. These metrics paint a clear picture of how your DLP program is performing and highlight where you need to make adjustments. They give you the hard data needed to demonstrate its value to leadership and ensure it remains a business enabler, not a bottleneck.
Key Metrics for a Healthy DLP Program
To get a genuine feel for your solution's effectiveness, you need to track metrics that cover both security enhancements and operational health. A well-tuned program strikes a fine balance between strong protection and smooth business operations.
Here are a few essential KPIs to keep a close eye on:
- Reduction in False Positive Rate: This is arguably the most critical metric for the long-term health of your program. A high volume of false positives leads to "alert fatigue," burning out your security team and creating a dangerous environment where real incidents might be overlooked. A consistent drop in this rate is a sure sign your policies are becoming more accurate.
- Mean Time to Resolve (MTTR) Critical Alerts: When a genuinely high-risk alert fires, how fast is your team able to investigate and close it out? A shrinking MTTR shows you have an efficient incident response process and a team that’s well-drilled on how to handle potential threats.
- Trend in Policy Exception Requests: Are employees constantly hitting roadblocks and asking for exceptions to DLP rules? A large number of requests often means your policies are too rigid and are getting in the way of legitimate work. This data is invaluable for finding that sweet spot between security and productivity.
The ultimate goal is to create a DLP system that operates almost invisibly in the background. It should protect sensitive data seamlessly without becoming a source of constant friction for your team.
Avoiding Common Mistakes SMBs Make
While tracking the right metrics is vital, it’s just as important to steer clear of the common pitfalls that can derail even the most sophisticated technology. For start-ups and SMBs, these missteps can be especially damaging, wasting precious resources and leaving dangerous security gaps.
Be on the lookout for these frequent errors:
- Creating Overly Restrictive Rules: It’s tempting to lock down everything from day one, but this approach almost always backfires. It grinds business operations to a halt and motivates employees to find insecure workarounds just to get their jobs done. A much better strategy is to start in a "monitor-only" mode to understand how data actually moves before you start enforcing blocking rules.
- Failing to Provide Employee Training: A DLP solution is a powerful tool, but it's not magic. If your team doesn't understand their role in protecting data, they will inevitably make mistakes. Regular, practical training is what turns your employees from a potential risk into your most valuable line of defence.
- Not Updating Policies as the Business Evolves: Your business isn't static, and your data protection needs aren't either. As you launch new products, expand into new markets, or bring new tools online, your DLP policies have to be reviewed and updated to keep pace. A "set it and forget it" mindset is a recipe for failure.
Your DLP Questions, Answered
Dipping your toes into the world of Data Loss Prevention can feel a bit overwhelming, especially when you're running a growing business and need every investment to count. Let's tackle some of the most common questions we hear from founders and leaders at startups and SMBs.
Are DLP Solutions Too Expensive for a Startup?
They used to be, but that's changed. Modern, cloud-based DLP solutions are a world away from the clunky, expensive enterprise systems of the past. They’re built for businesses like yours, with flexible subscription pricing that scales as you grow.
The real question is, what's the cost of not having one? When you consider the painful fallout from a single data breach—regulatory fines, lost deals, and a permanently damaged reputation—a well-chosen DLP solution quickly becomes one of the smartest investments you can make in your company's future.
How Is DLP Different from a Firewall?
It's a great question, and the answer comes down to inside versus outside threats. Think of a firewall as the security guard at your building's main entrance. Its job is to check who’s coming in and out, stopping obvious threats at the perimeter.
A DLP solution, on the other hand, is the security team inside the building. It’s not just watching the doors; it understands what's valuable in each room and makes sure sensitive documents don't walk out, whether by accident or on purpose. You absolutely need both.
Will a DLP Solution Disrupt Our Business Operations?
A poorly implemented one definitely could, which is why a thoughtful, actionable rollout is crucial. The smart approach is to start in a "monitor-only" mode. This lets the system learn the natural flow of data in your company without blocking anything.
You get to see how your team actually works and can build practical rules that make sense for your business. Once it’s dialled in, a good DLP solution works quietly in the background, acting as a safety net that lets your team innovate and collaborate freely without putting sensitive data at risk.
Ready to turn compliance from a hurdle into a competitive advantage? Compli.st is an AI-powered platform built to help you breeze through security questionnaires, automate compliance for frameworks like ISO 27001 and SOC 2, and prove your security commitment to enterprise clients. Start closing deals faster and building trust from day one. Visit the Compli.st website to learn more.